What is Gobuster?
Gobuster is a brute-force scanner tool to enumerate directories and files of websites. It will also assist in finding DNS subdomains and virtual host names. Gobuster is written in the Go programming language and is designed to function similarly to other tools like Dirbuster. Go is a very fast language and can be used in a command-line interface. A brute-force technique is a trial-and-error method of finding an answer to a solution. This innately means Gobuster is a “loud” enumerator that can be more easily detected by an Intrusion Detection System (IDS). Gobuster will not recursively enumerate directories, so it’s a good idea to run Gobuster again on any discovered directories. Overall, Gobuster is an excellent tool for enumerating web applications at the beginning of a pentest.
How to Install in Linux OS
First, we need to install the tool itself.
sudo apt install gobuster
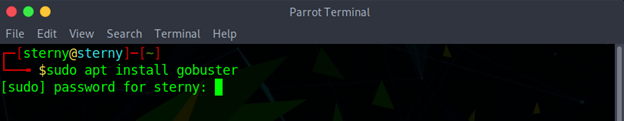
Our next step is to get the dictionaries that we will use to populate our enumeration.
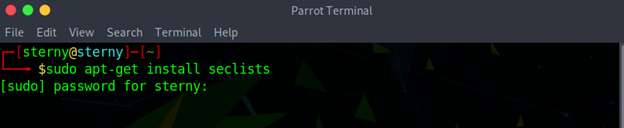
sudo apt-get install seclists
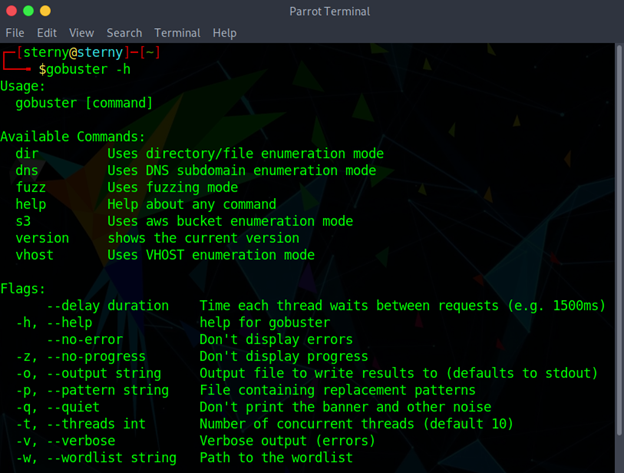
Using Gobuster
gobuster -h
We will examine the options that we can use with Gobuster. We can use the dir (directory or file), dns (subdomain), s3 (aws bucket), fuzz, or vhost options to define what scanner type we will use.
The next options are to choose the flags we will use to further define our scanner.
DIR mode
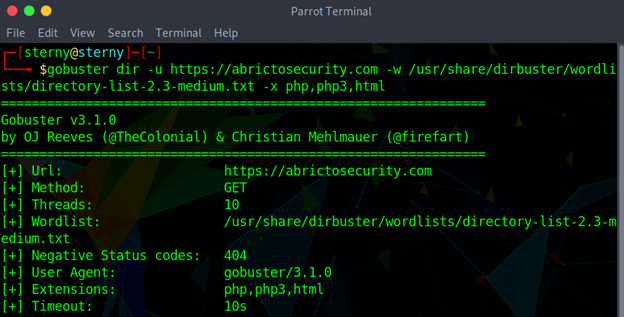
Dir mode is used to enumerate URLs for directories and files. This mode will be used to find content within a known target domain or subdomain. Gobuster will uncover hidden directories or files. -u is the URL that will define our target domain. -w is the wordlist we use to help identify the names of possible common directories or file names. -x are the string extensions we are expecting to find.
gobuster dir -u <url> -w <wordlist.txt> -x <file_extensions>
Example: gobuster dir -u abrictosecurity.com -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x php,php3, html
DNS mode
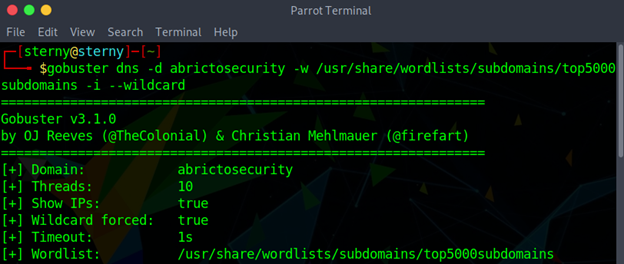
DNS mode is used to enumerate subdomains. -d is the identifiable target domain. -w is the wordlist that we will use to define our possible subdomain name list. -i will show the IP address. –wildcard allows parameters to continue even if there is a Wildcard DNS. This means a result will post, even if the results are from the same IP address.
gobuster dns -d <domain> -w <wordlist.txt> -i --wildcard
example: gobuster dns -d abrictosecurity -w /usr/share/wordlists/subdomains/top5000subdomains -i –wildcard
VHOST mode
VHOST mode or Virtual host brute-forcing mode will find virtual hosts within the domain. Virtual Hosting occurs when a domain is hosting other domain names on a single server or multiple other servers. This allows companies to share resources on a single server. This works by having Gobuster visit a URL and check the associated IP address. -v is for verbose mode. -u defines the target URL. -w is the wordlist that can help enumerate common virtual host site names. -o will output the results to an assigned file.
gobuster vhost -v -u <url> -w <wordlist.txt> -o <output_file.txt>
example: gobuster vhost -v -u https://abrictosecurity.com -w /usr/share/wordlists/subdomains/top5000subdomains -o vhostlist.txt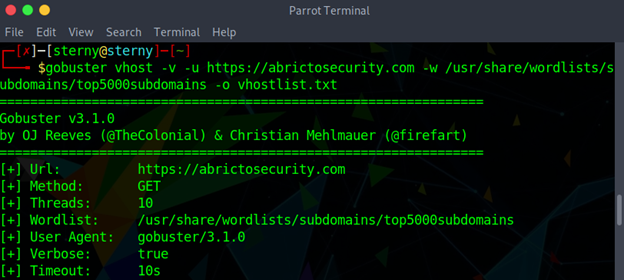
S3 Mode
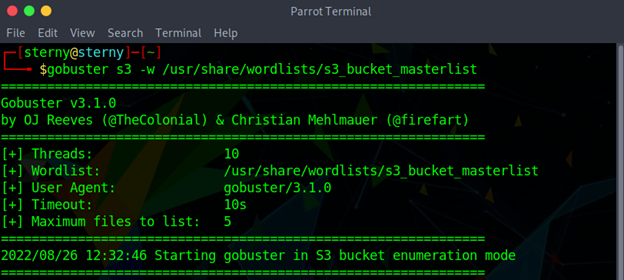
S3 mode will enumerate publicly available Amazon Web Service (AWS) S3 buckets. While Gobuster can help determine the names of the potential S3 buckets, it does not indicate that the buckets are able to be accessed or modified. You may still be able to use the information to access files available such as web support, logs, videos, or images. -w is the wordlist to define the names we will look to enumerate.
gobuster s3 -w <wordlist.txt>
example: gobuster s3 -w /usr/share/wordlists/s3_bucket_masterlist
Other Useful Flags
-e : completes printing the URL from enumerated directories
-n : will print results without the status code
-k : skip SSL verification
-t : assign the number of threads that will be used during enumeration
-r : allows redirection from one HTTP request to another
-p : allows proxy URLs to be used for requests on port 1080. This port can be changed in the URL.
-timeout : allows a timeout parameter to be set
-U <username> -P <password> : define a username and password for basic HTTP authentication mechanisms
References:
Special thanks to OJ Reeves for the amazing tool. Please visit his Github at https://github.com/OJ
The Gobuster tool Github can be found at https://github.com/OJ/gobuster
If you liked this post, check out other amazing cybersecurity blogs from our team here.