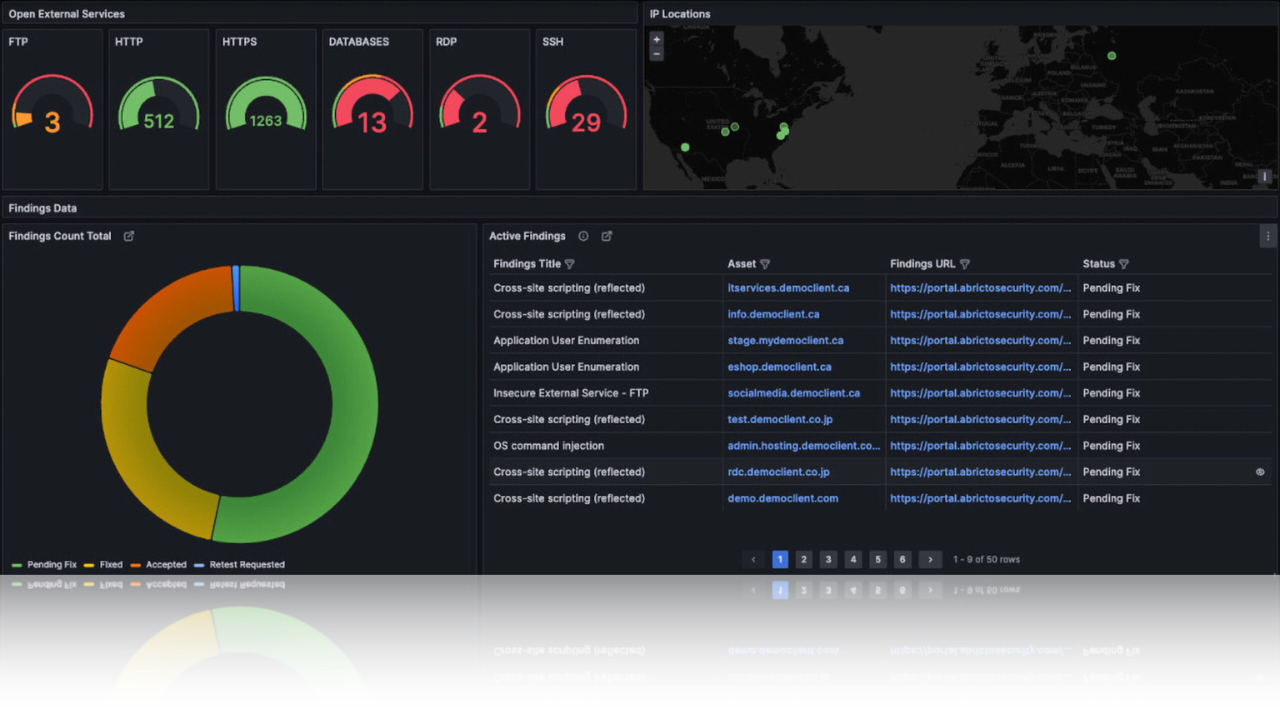
How Aardwolf Helps
Aardwolf is an enterprise security platform that continuously monitors external assets like domains, subdomains, and IPs to provide real-time visibility into exploitable vulnerabilities. It detects discrete attack vectors often missed by traditional tools and bug bounty programs. By tracking changes in an organization’s digital footprint and validating security controls, Aardwolf helps reduce attack surface and strengthens security posture with actionable insights.
Gain Full Visibility Over External Risks
As your infrastructure grows, keeping track of every internet-facing asset becomes more complex. Unmonitored assets are easily exposed to threat actors. Aardwolf provides full visibility across your entire external attack surface, identifying where vulnerabilities exist so you can address them before they’re exploited.

Detect Hidden Threats Beyond Standard Scans
Network scans typically miss critical application-layer vulnerabilities, leaving gaps in your defenses. Aardwolf goes beyond traditional scanning methods, detecting hard-to-find risks in applications, DNS, cloud services, code repositories, and more. Don’t let hidden vulnerabilities leave your systems open—get a complete assessment with Aardwolf.
Optimize Risk with Continuous Monitoring
With your external environment constantly evolving, managing risks across the enterprise can feel like a losing battle. Aardwolf continuously inventories your assets and highlights the most critical vulnerabilities, helping you prioritize the risks that matter most and take swift, targeted action.

Use Cases
Protects Externally Facing Systems
Quickly detect exposed management services in cloud services like RDP, MySQL, and APIs, allowing your team to address security gaps before they’re exploited. This approach prevents unauthorized access and keeps systems secure.

Manages DNS, Subdomains, and Certificates
Identify outdated DNS records, exposed subdomains, and certificate issues, reducing the risk of hijacking and service outages while simplifying infrastructure management.
Safeguards Sensitive Information
Identify unsecured sensitive files, credentials, and API keys across cloud and public platforms, helping enterprises quickly resolve data exposures and protect sensitive information.
Secures Cloud Storage and Applications
Identify unsecured cloud storage and backdoor vulnerabilities in applications, allowing your security team to mitigate risks and maintain control over critical assets.
Up-To-Date Asset Inventory & Tech Stacks
Keep DNS, subdomains, certificates, and tech stack components like frameworks and software updated to prevent hijacking, outages, and vulnerabilities.
Delivers Actionable Security Insights
Gain real-time data through a customizable dashboard, enabling security teams to prioritize and address vulnerabilities faster, staying ahead of potential threats.
Aardwolf handles the discovery, identification and validation of external vulnerabilities.
No more false-positives and no more communication barriers.
Beyond the Technical
Aardwolf aligns with business objectives to support growth.

Reduce Financial Exposure
Preventing breaches lowers the risk of expensive fines, legal costs, and revenue losses, directly protecting your bottom line.
Boost Team Productivity
Automation frees up your security teams to focus on strategic initiatives, leading to quicker resolutions and fewer costly interruptions to business operations.

Maintain Regulatory Compliance
Meeting industry standards and avoiding compliance penalties ensures your business stays in good standing with regulators, reducing the risk of fines.
Safeguard Brand Value
Proactively preventing security incidents protects your brand’s reputation, keeping customer trust intact and supporting long-term business growth.
Prevent Costly Downtime
Detecting and fixing issues before they impact services minimizes downtime, ensuring smooth business operations and preventing lost revenue.

Support Scalable Growth
As your organization grows, Aardwolf scales with you, allowing your enterprise to expand without increasing the complexity or cost of security management.