Our team researches and documents bleeding-edge security concepts and hacking techniques.
This blog explores these topics and more to keep you informed.
HomeLab Series: Proxmox on Refurbished Servers
Why and What Setting up a homelab can feel overwhelming at first. With an abundance of guides, opinions, and technical information available, taking the initial step may seem challenging. However, the long-term benefits far ...
Building Your Own Homelab Testing Environment
I do a lot of tool building and research in the container space for Windows. This often requires something called nested virtualization. What is Nested Virtualization? In simple terms, nested virtualization is the ability ...
OSINT: From Basic Tools to Advanced Techniques
What exactly is OSINT? Broadly speaking, OSINT—or Open-Source Intelligence—refers to the gathering, evaluation, and analysis of publicly available information to answer a specific question. This information can come from various sources, including public records, news ...
Understanding the Difference Between a Compiler and an Interpreter
When you write a program in a high-level language like Python or C++, you are using something that makes sense to us as humans, but not to your computer. It's similar to speaking a ...
Attacks You Should Know About: Cross-Origin Resource Sharing
Welcome to the second installment of our "Attacks You Should Know About" series! This blog provides valuable insights for both novice and experienced cybersecurity professionals on common attacks and vulnerabilities. Today, we examine cross-origin resource ...
HTB: Blocky Walkthrough
Blocky is a Linux machine with an easy-to-medium difficulty rating. It contains several intentional rabbit holes, including WordPress components, plugin directories, and PhpMyAdmin, which can initially mislead the enumeration process. Nmap Scan ┌──(kali㉿kali)-[~] └─$ nmap ...
Understanding #s in C Programming Part 1: Macros and Conditionals
Within C programming, there are many commands that start with the # symbol that are used as placeholders for the C preprocessor. These hash-directives can be used to define tokens for substitution, pull in header ...
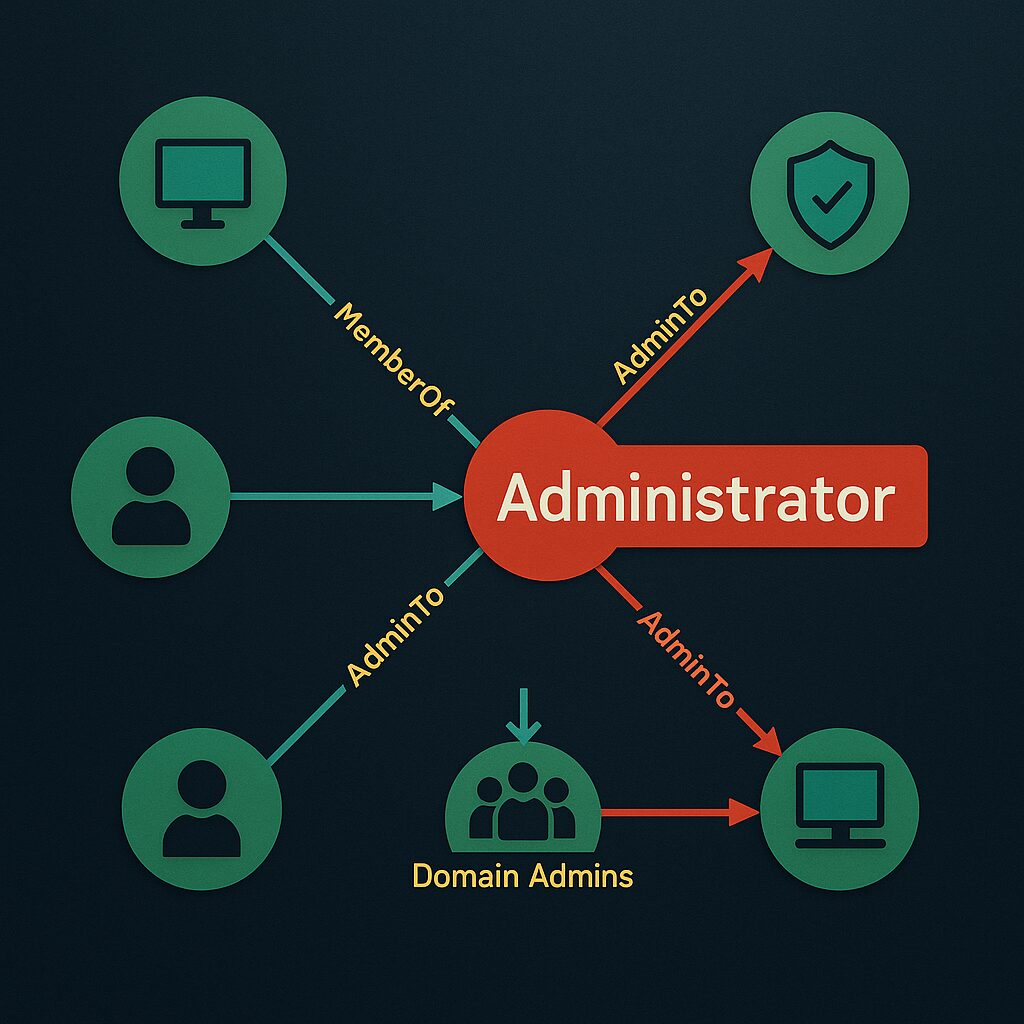
HTB: Administrator Walkthrough
Administrator is a Windows-based machine rated as medium difficulty on Hack The Box. It’s designed to mimic a real-world Active Directory setup, giving the opportunity to dig into SMB enumeration, map out attack paths with ...
Attacks You Should Know About: Clickjacking
Welcome back to another installment of "Attacks You Should Know About"! If you’ve been following along, you already know that web applications are full of potential vulnerabilities. Today, we’re diving into one of the more ...