Introduction
Is your SaaS platform’s security armor full of chinks you’ve yet to discover? As we explore the essential role of application security in the SaaS sector, this article will cover why regular security audits are crucial and how overlooking them can lead to severe setbacks. By understanding common security pitfalls, the value of continuous monitoring, and the benefits of incorporating security into the development process, readers will learn how to safeguard their SaaS platforms effectively.
What is Application Security in the SaaS Context?
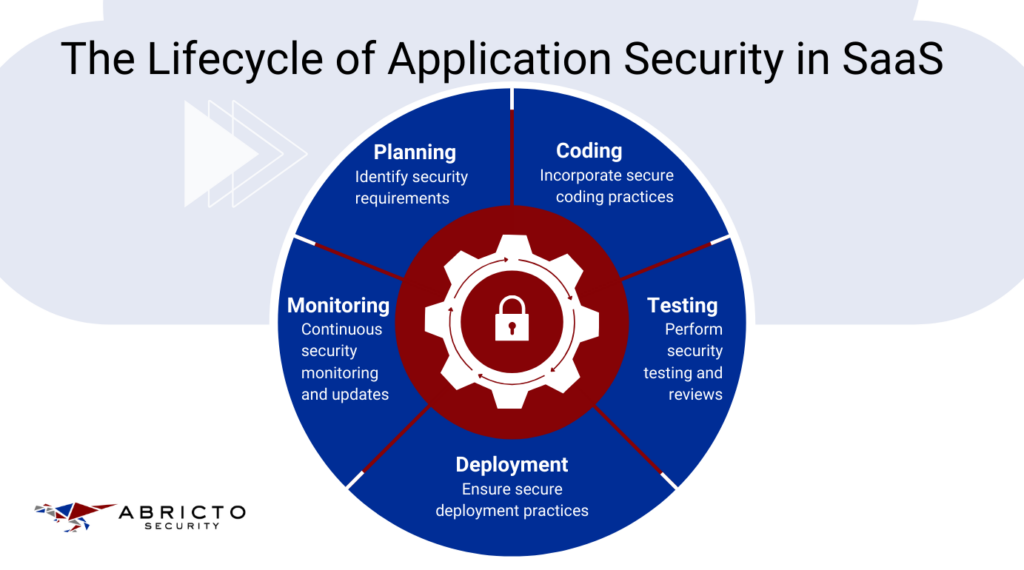
Within the SaaS domain, application security (AppSec) represents a strategic framework aimed at fortifying software against cyber threats. This is particularly vital for SaaS applications, which operate online and serve multiple clients, heightening the necessity for robust protection of both the application’s internal workings and the customer data it processes.
The AppSec process is comprehensive, entailing several essential phases:
- Planning: This foundational phase is about pinpointing the specific security needs and establishing a plan to address them. It’s about foreseeing potential risks and crafting a tailored strategy to mitigate them effectively.
- Coding: At this juncture, developers incorporate secure coding practices to build defenses into the app’s very DNA. It’s about writing code that’s not just functional but also resilient to attacks from the outset.
- Testing: Rigorous testing is conducted to uncover and rectify any security vulnerabilities, ensuring the application’s defenses are solid before it reaches the public.
- Deployment: Secure deployment practices are critical to prevent lapses in security when the application transitions from development to live environments.
- Monitoring: Continuous monitoring is imperative for detecting and responding to emerging threats promptly. It ensures that security measures are always up to date and effective against the latest threats.
Each phase in the AppSec lifecycle is crucial to the overall security posture of a SaaS platform, serving to protect customer data and preserve the integrity and continuity of service.
The Importance of Regular Security Audits
Regular security audits are an indispensable component of a robust SaaS security strategy, yet they are often underpriorized in the race to deliver new features and accelerate business growth. Such oversight is a significant misstep that can leave a SaaS platform’s defenses weakened against emerging threats.
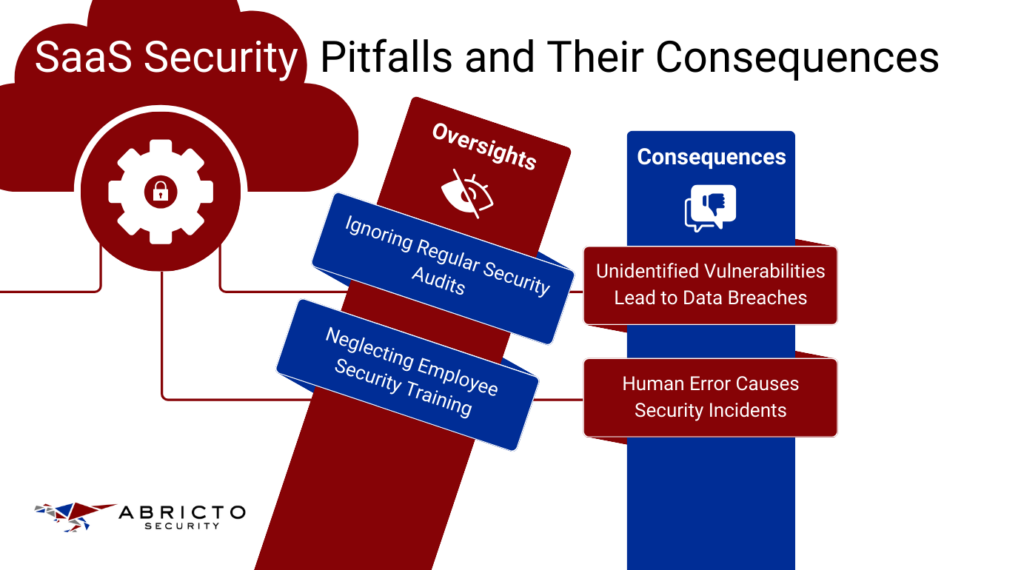
Oversights: Ignoring Regular Security Audits
Frequent security audits are a must for identifying vulnerabilities that could compromise a SaaS application. When audits are not conducted regularly, the application is left with unchecked weaknesses. As new features are added and existing ones are updated, the opportunity for attackers to exploit these vulnerabilities increases, making the platform susceptible to attacks that could have been prevented.
Consequences: Unidentified Vulnerabilities Lead to Data Breaches
The most direct fallout from skipped audits is the manifestation of application vulnerabilities. Unidentified vulnerabilities can lead to severe breaches, spilling sensitive customer information and incurring hefty fines under data protection regulations. The legal entanglements that follow can be a nightmare, with the potential to inflict lasting damage on a company’s finances and reputation.
Oversights: Neglecting Employee Security Training
Another critical pitfall is the lack of regular security training for employees. When team members are not trained to recognize and respond to security threats, they become the weakest link in the security chain. Without ongoing education, employees can inadvertently compromise the application’s integrity.
Consequences: Human Error Causes Security Incidents
Human error is often a significant contributor to security incidents. Employees unaware of best security practices may fall prey to phishing attacks or unknowingly expose the system to threats. Such incidents can disrupt operations and damage the trust that customers place in a SaaS provider’s ability to safeguard their data.
The Role of Continuous Security Monitoring
Continuous security monitoring is the practice of persistently overseeing and assessing the security posture of SaaS applications to identify and mitigate threats in real-time. This approach ensures that security measures evolve alongside new threats and the changing landscape of SaaS applications, making it an essential aspect of modern cybersecurity strategies.
SaaS companies can utilize a combination of tools and practices designed for real-time threat detection and response to implement continuous security monitoring in SaaS applications. These include:
- Automated security scanning tools are used to scan for vulnerabilities regularly.
- Intrusion detection systems (IDS) to monitor network traffic for suspicious activity.
- Security information and event management (SIEM) systems for aggregating and analyzing security logs.
- Implementation of endpoint detection and response (EDR) solutions.
- Regularly update and patch software to address known vulnerabilities.
The benefits of early detection of security vulnerabilities are significant. Identifying and addressing vulnerabilities before they can be exploited reduces the risk of data breaches, thereby protecting customer data and maintaining trust.
Common Security Vulnerabilities in SaaS Applications
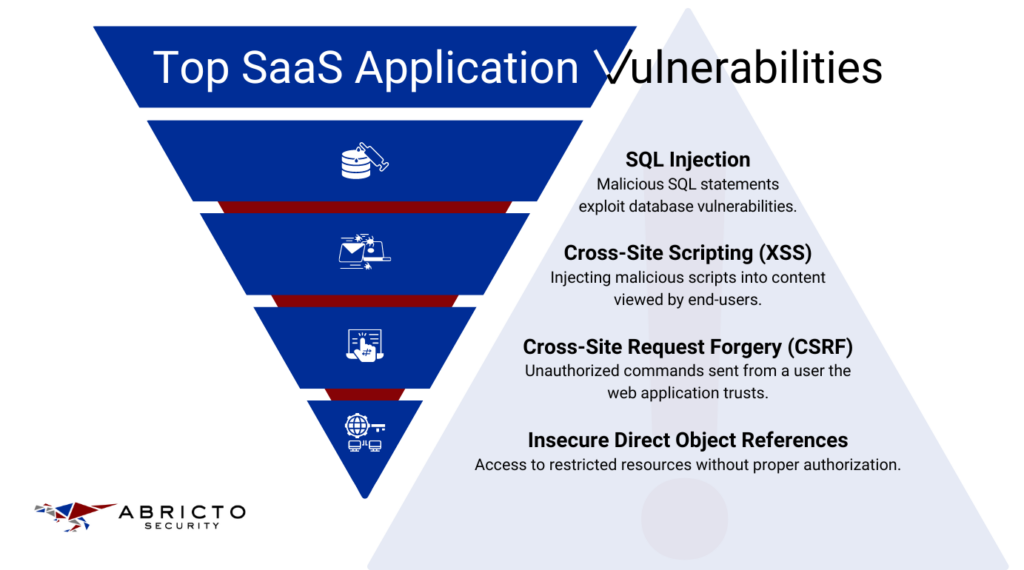
While offering scalable and efficient solutions, SaaS platforms are not immune to security vulnerabilities. Common issues such as SQL injection and cross-site scripting (XSS) pose significant risks, potentially allowing attackers to bypass authentication, access sensitive data, or execute malicious scripts.
- SQL Injection: This occurs when attackers manipulate SQL queries through user input areas of a SaaS application to gain unauthorized access to or manipulate the database. It can lead to data theft, loss, or corruption.
- Cross-Site Scripting (XSS): XSS vulnerabilities enable attackers to inject malicious scripts into web pages viewed by other users, potentially stealing data, hijacking user sessions, or defacing websites.
- Cross-Site Request Forgery (CSRF): In this attack, authenticated users are tricked into executing actions on a web application in which they’re currently authenticated, potentially leading to unauthorized changes or data breaches.
- Insecure APIs: Many SaaS platforms rely on APIs for communication between services. Insecure APIs can expose sensitive data or allow unauthorized access if not properly secured.
- Misconfiguration: Improper setup of cloud services and platforms can expose SaaS applications to risks of data breaches and unauthorized access.
To safeguard against these vulnerabilities, SaaS providers must adopt a security-first mindset. Additionally, implementing secure coding practices, such as input validation, encoding outputs, and using prepared statements for database access, can prevent many common vulnerabilities.
Creating a Culture of Security Awareness
Building a security-aware culture within a SaaS organization is about more than just protocols and passwords; it’s about making sure every individual understands their role in safeguarding the company’s digital assets. This collective understanding and effort can create a formidable barrier against potential security threats.
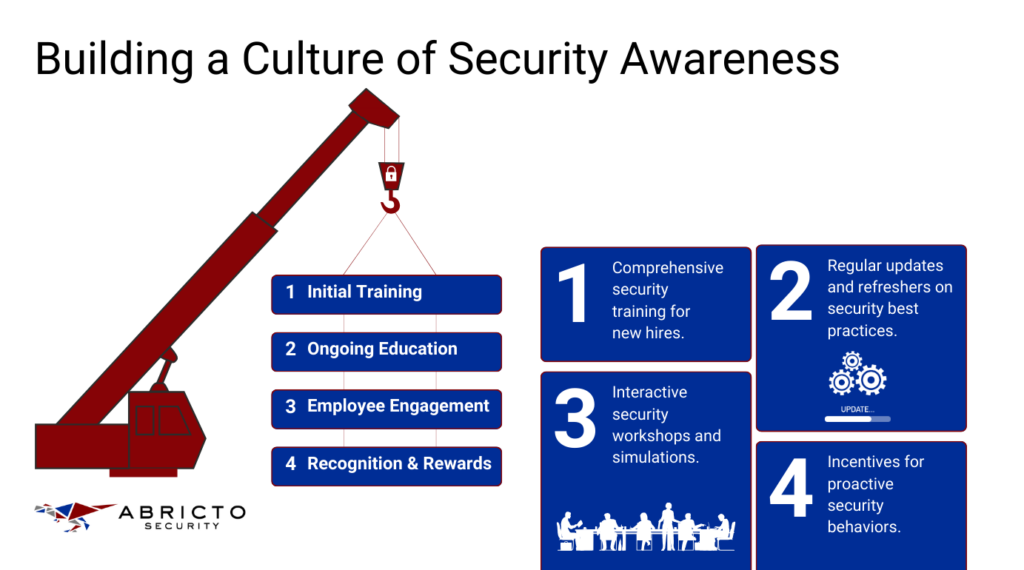
Training for New Hires
The onboarding process is the ideal starting point for instilling security awareness in new team members. A well-structured training program for new hires can lay a strong foundation for security practices.
It should cover the company’s security policies, the rationale behind them, and the specific actions employees are expected to take to maintain security.
Using real-world scenarios and recent case studies can illustrate the importance of these practices and help new hires understand the direct impact their actions can have on the company’s security.
Regular Updates and Refresher Training
The cybersecurity landscape is constantly evolving, and so should the knowledge of your team. Regularly scheduled updates and refresher training sessions ensure that all employees are aware of the latest threats, the newest compliance requirements, and the most recent company policies.
These sessions should be mandatory, engaging, and tailored to different roles within the company, providing relevant updates that keep security at the forefront of everyone’s mind.
Interactive Workshops
Interactive workshops take training a step further by engaging employees in active learning experiences. These sessions can involve hands-on activities, simulations of security incidents, and team-based problem-solving scenarios that relate to actual risks the company might face. Interactive workshops are a great way to reinforce theoretical knowledge, test how employees might respond to real-life security challenges, and encourage team collaboration for maintaining a secure working environment.
Positive Incentives for Following Good Security Practices
Finally, positive reinforcement can be a powerful tool in promoting good security habits. Recognizing and rewarding employees for proactive security behaviors, such as reporting suspicious activities, can encourage others to follow suit.
Incentives can take many forms, from public acknowledgment in company meetings to tangible rewards like bonuses or gift cards. Whatever the form, they should aim to reinforce the value the company places on security and motivate individuals to take ownership of their role in the company’s security efforts.
Conclusion
In this article, we’ve uncovered why it’s important to perform regular security checks, keep a close watch on your SaaS platform, and weave security into your app’s creation and growth. Getting these right means you’re well on your way to protecting your users’ data, earning their trust, and avoiding interruptions to your service. But if you don’t have security experts internally, managing this can seem like scaling a mountain without gear.
That’s precisely the gap our AppSec as a Service aims to fill. We offer specialized support and deep expertise to simplify these complex tasks for you.
Connect with us, let’s talk about customizing our services to fit what your SaaS app needs to stay safe and sound.
