If you’ve ever conducted a web application penetration test, been involved web page development, or hovered within the IT space, you may have heard of a software called WordPress. However, did you know this software is a highly vulnerable attack surface for threat actors? WPScan is a tool that you can add to your penetration testing arsenal that can assist in scanning WordPress for vulnerabilities.
What is WordPress?
WordPress is a content management system (CMS) that was initially developed for blog publishing, but has evolved into a tool used to create a variety of web application content. It allows a user to develop their website behind a user-friendly interface and updates the source code as the user makes changes. This is a characteristic of WordPress that makes it chose over other forms of web page development tools. Per the WordPress organization, approximately 43% of the entire web is powered by WordPress. This equates to nearly half of the production web pages you navigate to are using open-source software. While this is certainly a testament to its capabilities and utility in creating web pages, it consequently provides a large attack surface for hackers and threat actors to exploit.
How can WordPress be exploited?
There are a number of different tools that can be used to exploit WordPress. The most popular tool, and one we will be focusing on today, is wpscan. Some useful functions wpscan can perform include:
- Enumerating users, WP version, and PHP version
- Password brute forcing
- Target popular and vulnerable WP plugins
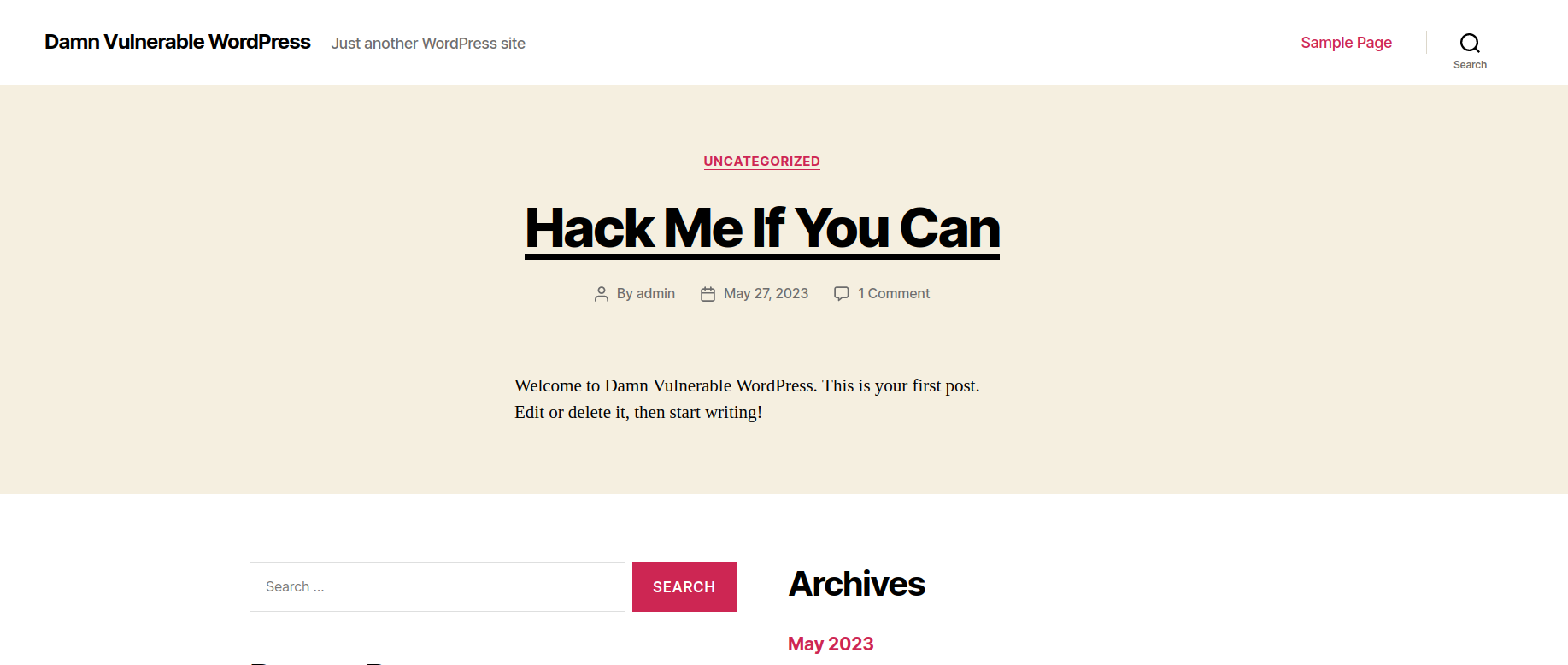
For this demonstration, we will be using the “Damn Vulnerable WordPress” web application. For this use case, it is quite obvious that this web page is being powered by WordPress.
Identifying WordPress on a server
There are a few methods to identify if WordPress is running on a web server. These include:
- Browser extensions (BuiltWith, Wappalyzer)
- Port scanners (nmap)
- nmap -sV –script http-wordpress-enum <target>
- URL extensions (<URL>/wp-admin, <URL>/login, <URL>/admin, etc.)
In this case, when we scroll to the bottom of the home page, we can see that the page discloses that it is being powered by WordPress.
Version and Plugin Enumeration
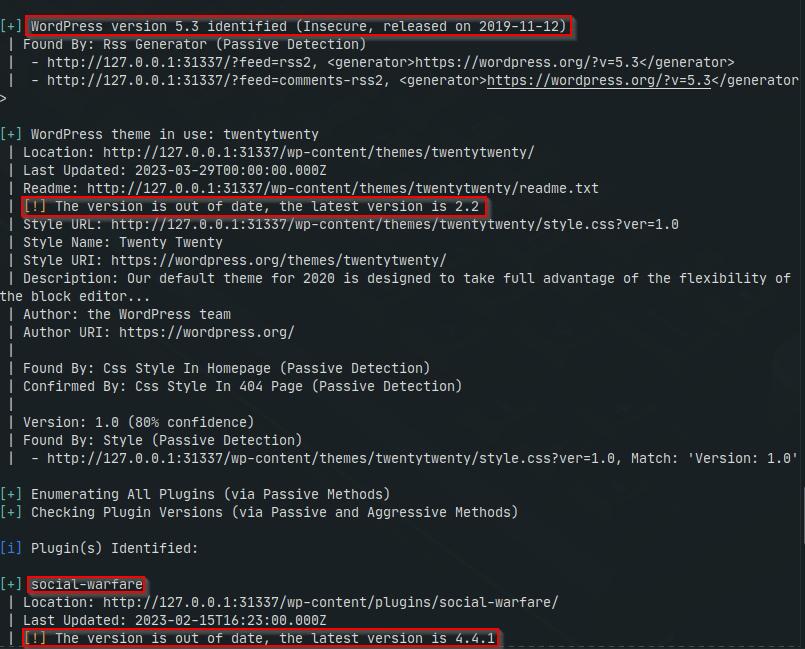
Now that we’ve identified the webpage is running WordPress, we can use wpscan to enumerate other useful information, such as plugins and the current version. We run this with the following command:
- wpscan –url <target>
User Enumeration
As mentioned earlier, one of the biggest giveaways that a web application is running WordPress is if you can access the admin login page. While the webpage administrator can make changes to the naming convention of the login URL, you can try appending the following to your target’s URL:
- /admin
- /login
- /wp-login.php
Once reaching the WordPress login page, you will be prompted for a username and password. The default credentials for WordPress are ‘username’ and ‘password’. However it is highly likely that those credentials have been changed at some point in time. Nevertheless, it is always worth trying default credentials.
The is where wpscan’s user enumeration comes in handy. We can run the following command to enumerate users:
- wpscan –url <target> –enumerate u
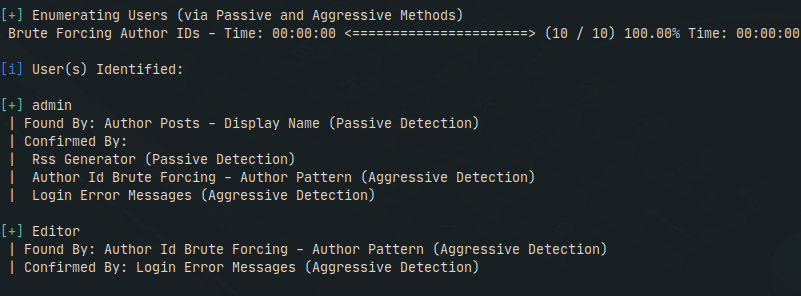
Look at that! We were already able to enumerate the administrator account for WordPress.
Password Brute Forcing
Once we’ve collected valid usernames, we’re halfway to obtaining an account that could grant access to a website login page. Fortunately, wpscan has a feature that allows you to test a list of passwords against any users you enumerated. To do this, we will run the following command:
- wpscan –url <target> -P <path/to/your/wordlist.txt>
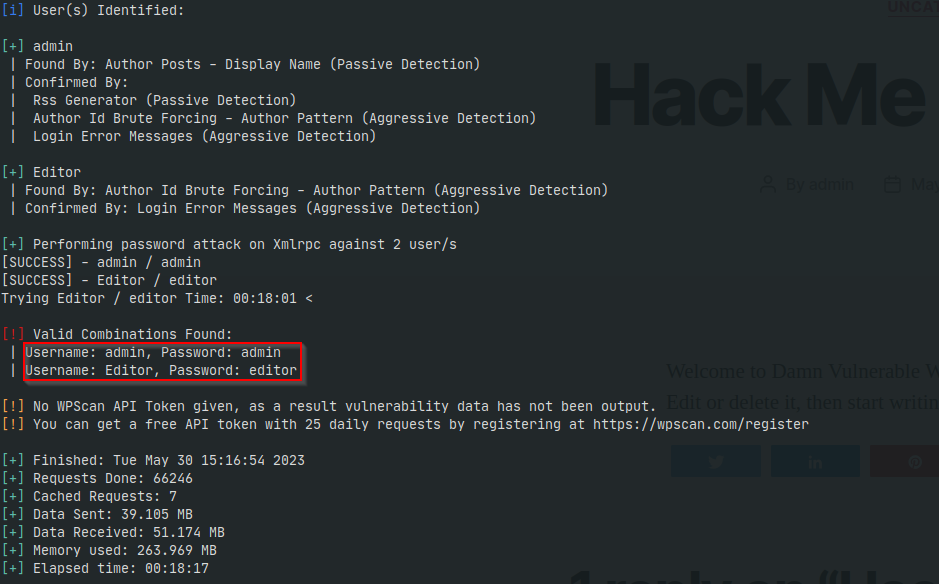
We can see that we successfully identified the passwords for both the admin and editor accounts. Now, if we navigate to the <target>/wp-admin page and try logging in with credentials:
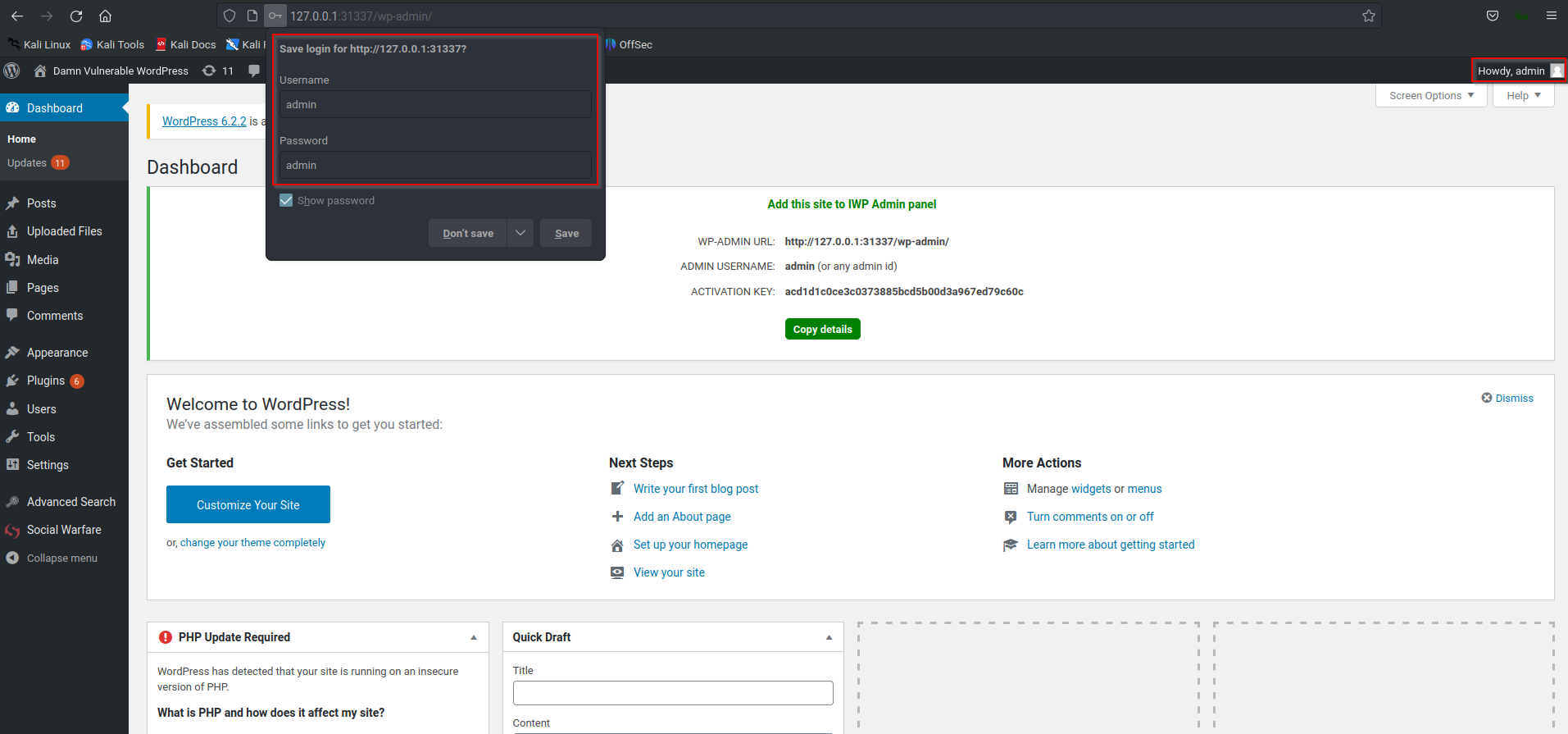
We have successfully logged into the administrator WordPress account for this web page. From here on out, there are tons of other exploits that could be implemented (XSS, SQL injections, remote shells, etc.)
Cheat Sheet
Here are some other useful flags you can use when running wpscan:
- Display help menu to view all commands: -h
- Change detection from passive, aggressive, and mixed: –detection-mode <mode>
- Use a random user-agent on a scan (useful when blocked by a WAF): –random-user-agent
- Select a list of users to be targeted during a password brute force attack: -U <path/to/your/userlist.txt>
- Different enumeration options:
- Vulnerable plugins – vp
- All plugins – ap
- Popular plugins – p
- Vulnerable themes – vt
- All themes – at
- Popular themes – t
- Config backups – cb
- Db exports – dbe
Warning – Please do not try these tactics and techniques on any domain, without explicit permission from the domain owner. This information is solely for educational purposes, and Abricto Security is not responsible for any individuals that use these tactics and techniques in any sort of unauthorized or malicious manner.