What exactly is OSINT?
Broadly speaking, OSINT—or Open-Source Intelligence—refers to the gathering, evaluation, and analysis of publicly available information to answer a specific question. This information can come from various sources, including public records, news media, libraries, and social media platforms. OSINT primarily serves as a way to discover information, but its use depends on the individual. It can be employed for a variety of purposes, whether it’s reconnecting with someone after years apart or for more malicious intents. In fact, people engage in OSINT every day without even realizing it; for example, simply searching for someone’s name online to learn more about them is a basic form of OSINT. While this is one of the simplest applications, conducting an in-depth OSINT investigation requires knowledge of specialized tools, techniques, and strategies to effectively gather and analyze data. There are numerous online services designed to help uncover information about individuals or entities, and these tools can be categorized based on their functionality.
Google Dorking Basics
Google Dorking works by directing Google’s search algorithm to retrieve targeted data based on specific criteria. It is particularly useful for locating specific file types, searching within a particular website, and finding keywords in URLs, page text, or metadata. Examples of Google Dorking operators include:
- filetype: – Searches for a particular file extension
- intext: – Finds web pages containing a specific keyword or phrase in the page body
- inurl: – Searches for URLs containing a specific word or phrase
Here’s what it looks like when we use all these keywords together in a Google search: we’re looking for sites with a PDF filetype, the word “admin” in the URL, and the word “admin” in the page body.

By leveraging these search operators, OSINT practitioners can uncover a wealth of publicly accessible information that might otherwise be hard to find. Numerous online services are available to help gather information about individuals or entities, and these tools can be categorized based on their functionality.
Username and Link Search Tools
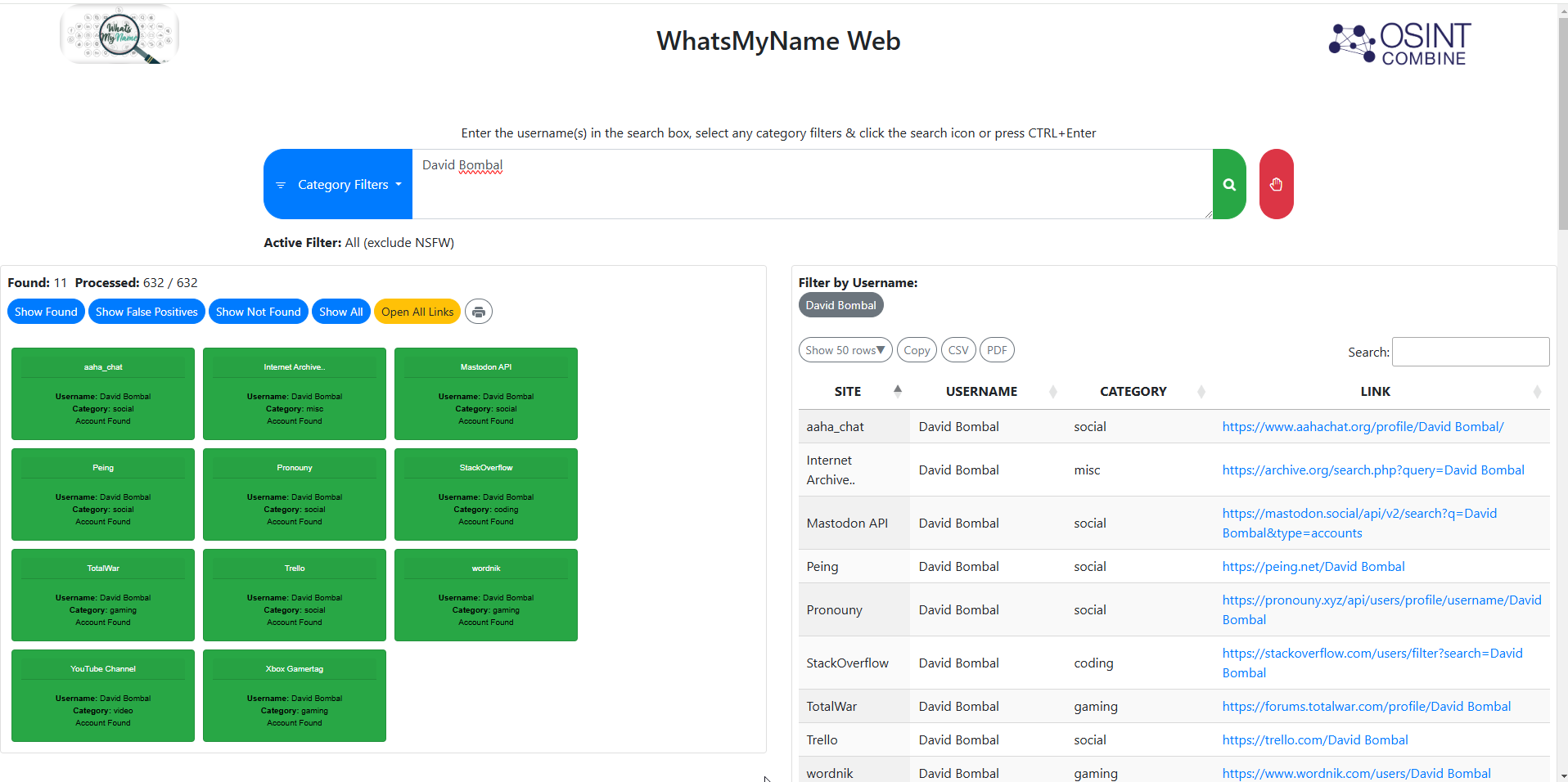
Some tools specialize in finding relevant links associated with a specific username or name. While this concept is similar to Google dorking, these tools help categorize and organize the results. One such tool is WhatsMyName.app, which searches for links where the provided username or name appears within the URL.
For example, if we search for David Bombal, we can apply filters to focus on specific types of sites, such as those related to music or finance. In this instance, we search across all categories. Once executed, the tool sends requests from your browser to various websites, looking for matches in the URLs. However, some results might be false positives—links that lead to inactive pages—which require manual verification.
Reverse Image Search Tools
Reverse image search enables users to find information using an image instead of text. Tools like Search by Image—a Google extension—allow you to perform simultaneous searches across multiple search engines with just a right-click. For example, if you have an image of a monument and want to identify its location, this extension streamlines the process by searching across several platforms at once, eliminating the need to manually upload the image to each one.

People Search Databases
Some websites provide detailed personal information when given sufficient input. A notable example is TruePeopleSearch.com, which can reveal potentially sensitive details such as home phone numbers, addresses, property values, and even possible relatives, as shown below.
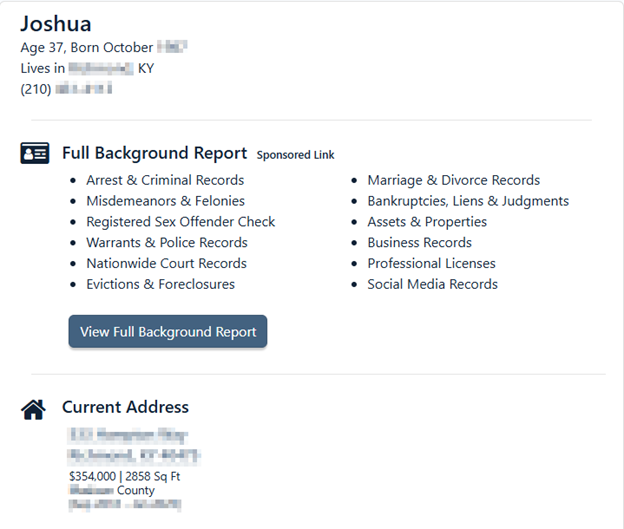
This tool can be useful for gathering basic personal data, which can then serve as a pivot point for uncovering further information. Each of these OSINT tools has its own use case, yet they all share the same fundamental purpose: helping users efficiently gather publicly available data.
So far, we’ve discussed various OSINT tools and techniques, but we haven’t yet delved into why understanding OSINT is crucial. Using OSINT effectively goes beyond simple data gathering—it demonstrates how publicly available information can be leveraged for both beneficial and malicious purposes. Many people assume that finding personal information requires advanced hacking skills, yet OSINT tools make it surprisingly accessible to anyone. You might have noticed that I haven’t covered tools like theHarvester or recon-ng, which require installation and manual execution—that was intentional. The tools I’ve shown so far, such as Google Dorking, username searches, reverse image searches, and people search databases, are all free to use and don’t demand special technical expertise. This underscores how easily OSINT can be exploited for personal gain, whether for ethical purposes like reconnecting with old contacts or investigating cybersecurity threats, or for more malicious activities like doxxing, social engineering, and cyberstalking.
