Introduction
Are you looking to improve your company’s SaaS security without all the hassle? Switching to Application Security as a Service (ASaaS) can be a game-changer. It offers continuous monitoring, expert support, and automated compliance, all tailored to your needs. In this guide, you’ll learn how to assess your current security, pick the right ASaaS provider, integrate new tools, and keep improving your security. Follow these steps to make your transition smooth and successful.
Preparing for the Transition
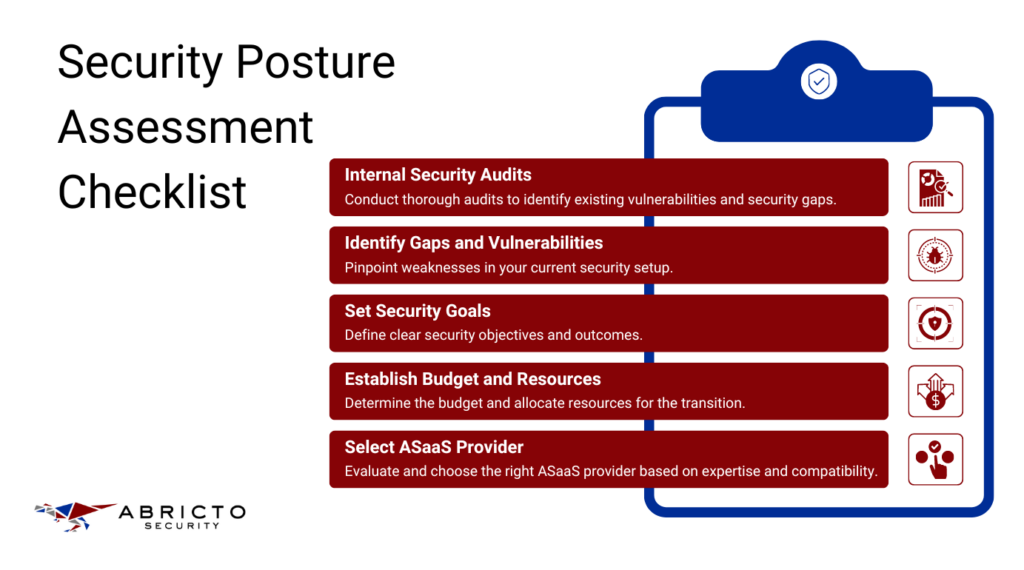
Assessing Current Security Posture
Start by conducting thorough internal security audits. This step is essential for identifying your application’s existing vulnerabilities and security gaps. A detailed audit helps you understand your current security posture and highlights areas that need immediate attention.
Once you understand your vulnerabilities, setting clear security objectives is important. Define what you aim to achieve with your security measures. These goals should be specific, measurable, and aligned with your overall business objectives to ensure they effectively address your security needs.
Selecting the Right ASaaS Provider
Choosing the right ASaaS provider is crucial for a successful transition. Assess potential providers based on their expertise, experience, and how well their services align with your company’s specific needs. Look for providers with a proven track record in the industry and who offer solutions that fit seamlessly with your existing infrastructure.
After narrowing down your choices, thoroughly review case studies and testimonials from other companies who have used the provider’s services. Schedule interviews to ask detailed questions about their approach and support. This process will help you decide and select the best provider for your company’s unique requirements.
Initial Engagement with ASaaS Provider
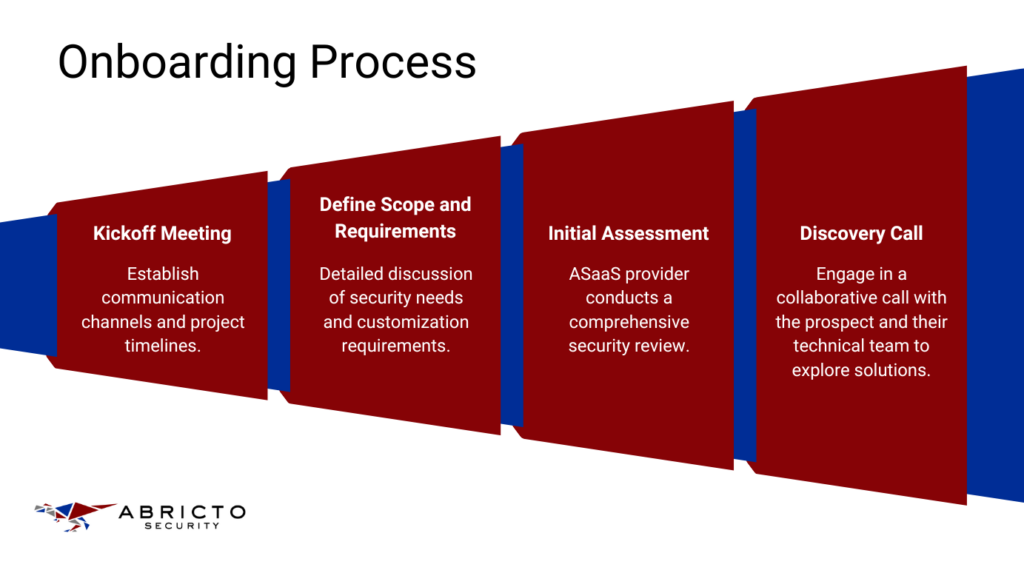
Onboarding Process
The kickoff meeting is the first step in your engagement with an ASaaS provider. During this meeting, you’ll establish communication channels and set project timelines. This is a great opportunity to align everyone involved and ensure all parties agree regarding expectations and deliverables.
During the kickoff meeting, you’ll need to discuss your security needs and any customization requirements. This conversation helps the ASaaS provider understand your specific security challenges and tailor their services to meet your company’s unique needs.
Security Assessment
The ASaaS provider will begin with an initial security review. This assessment will thoroughly evaluate your security measures, identify weaknesses, and highlight potential risks. It’s an important step to get a clear picture of your existing security posture.
Following the assessment, the provider will deliver a detailed report. This report will outline the identified issues and offer suggested actions to address them. Reviewing these recommendations carefully and discussing any questions or concerns with the provider is essential to ensure a solid understanding and effective implementation.
Technical Integration
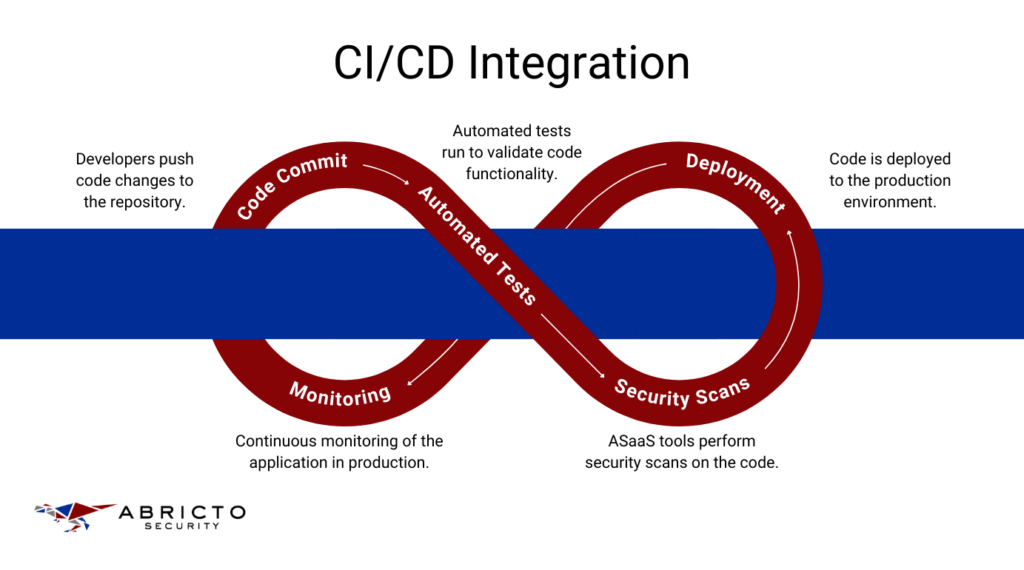
Infrastructure Integration
Embedding ASaaS tools into your CI/CD pipelines is a great way to keep security checks ongoing throughout development. By integrating security testing at every stage—from code commits to production —you can catch and address vulnerabilities early. This proactive approach helps ensure your applications remain secure while saving time and resources.
To make everything work smoothly, use APIs to connect ASaaS tools with your existing development and operational tools, like project management software and version control systems. This seamless integration ensures that security data flows smoothly across your systems, giving you a clear and unified view of your security setup and making management tasks easier.
Data Handling and Compliance
When moving sensitive data to the ASaaS platform, it’s important to keep it secure. Use end-to-end encryption during data transfer and ensure all data is encrypted while moving and stored. This protects your data from unauthorized access and ensures its confidentiality and integrity.
Make sure your ASaaS provider’s practices match industry standards and regulatory requirements. This means checking that they follow best practices for data protection, like GDPR, HIPAA, or other relevant regulations. Regular audits and reviews can help confirm compliance, which can help you avoid legal issues and build trust with your customers by showing your commitment to protecting their data.
Implementation and Deployment
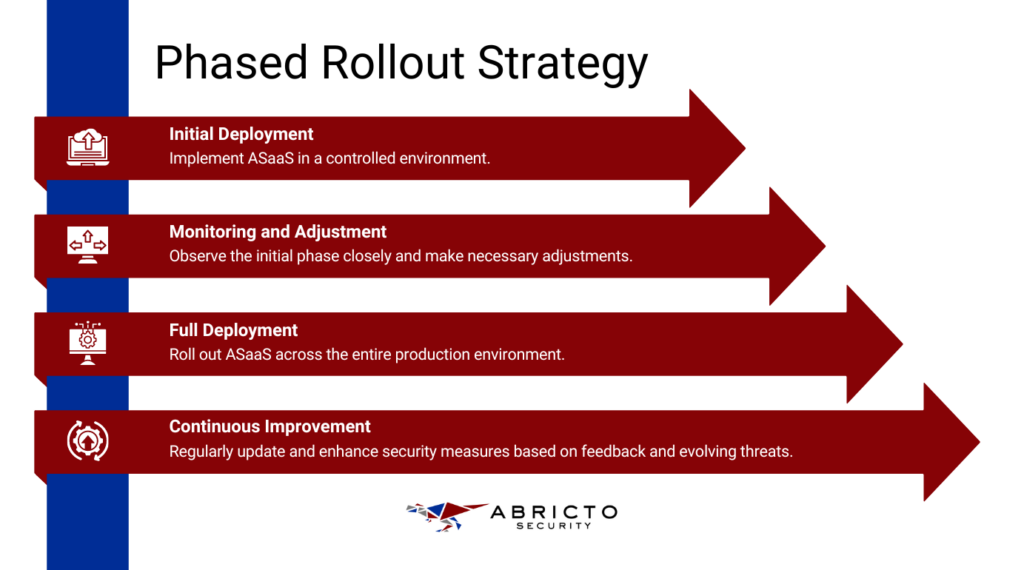
Ongoing Operations
Continuous Monitoring
With ASaaS, you can set up 24/7 monitoring to catch security threats as they happen. This real-time alert system allows you to respond to potential issues quickly, minimizing the impact on your operations and maintaining a high level of security. Constant vigilance ensures that any unusual activity is detected and addressed immediately, keeping your systems safe around the clock.
Scheduling regular security assessments is essential to maintain ongoing compliance and security. These assessments help you identify new vulnerabilities or security gaps that may have emerged over time. By conducting these periodic reviews, you can ensure your security measures are always up-to-date and effective, giving you peace of mind that your systems are protected.
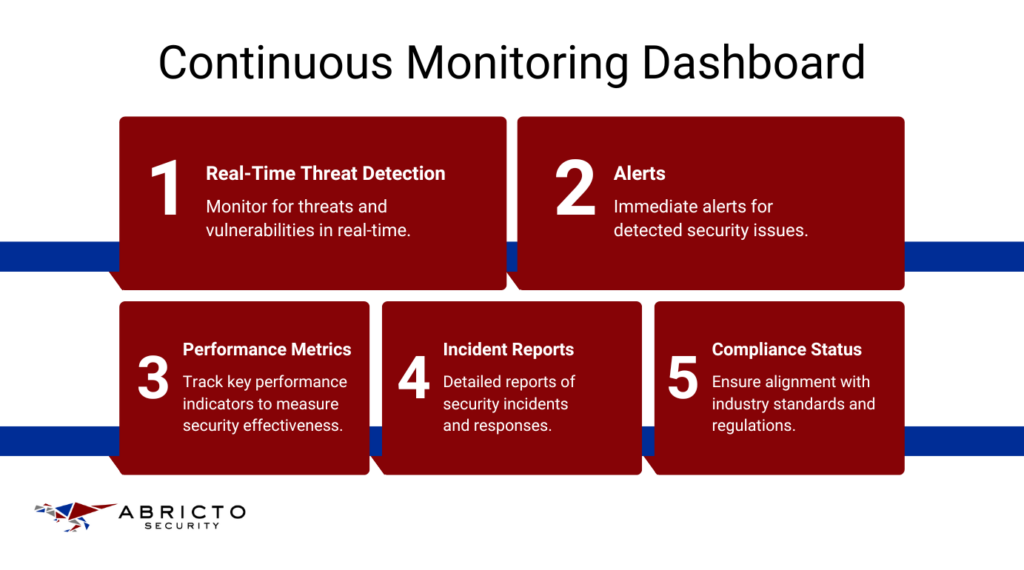
Incident Management
Developing and implementing a detailed incident response plan is crucial for effective security management. This plan should outline clear steps and procedures for your team during a security incident. Having a well-defined strategy helps your team react quickly and efficiently, reducing the potential damage and downtime caused by security breaches.
Keeping detailed logs and reports of all security incidents and responses is vital. These records provide valuable insights into the nature of the incidents and how they were handled, which can inform future improvements to your security practices. Thorough documentation is also important for compliance, helping you meet regulatory requirements and providing evidence of security measures during audits and reviews.
Post-Implementation Review
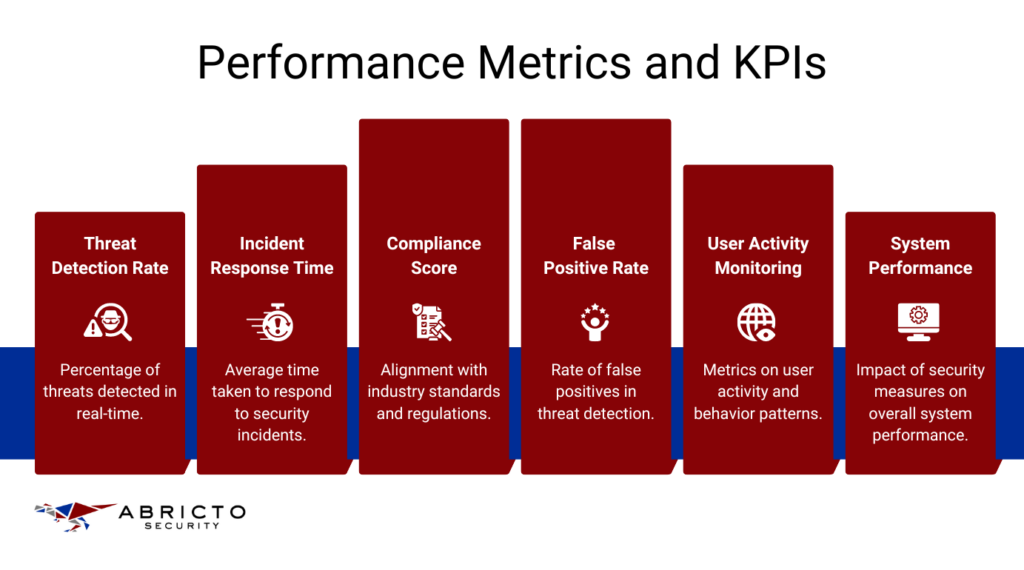
Performance Metrics
After implementing ASaaS, it is important to track key performance indicators (KPIs) to measure its effectiveness. These KPIs include metrics like the number of vulnerabilities detected and resolved, the speed of incident response, and overall system uptime. Monitoring these benchmarks helps you understand how well ASaaS works and identifies any areas needing improvement.
Collecting feedback from your development and security teams is essential for continuous improvement. Regularly check in with your teams for insights on the ASaaS implementation. This feedback can highlight any pain points or areas where the system could be enhanced, ensuring your security measures always evolve and improve.
Continuous Improvement
It is crucial to stay updated with the latest security trends and threats. Ensure your team receives ongoing training to keep their skills sharp and current. Regular updates to your security protocols and systems help you stay ahead of new threats and maintain a strong security posture.
Enhancing security measures based on emerging threats and evolving business needs is key to effective protection. This means regularly reviewing and updating your security policies, tools, and practices to address new vulnerabilities and improve overall security. By being proactive, you can ensure that your systems remain secure and resilient against potential threats.
Conclusion
We’ve outlined the key steps for moving to ASaaS: assessing your security, choosing the best provider, onboarding, integrating tools, and continuous improvement.
ASaaS helps you stay ahead of threats and protect your business. Ready to take your security to the next level? Contact us today to book a call and see how our ASaaS solution can secure your SaaS applications and help your business grow.
