Introduction
Do you find protecting your app from the latest security threats challenging? A lot of folks do. This is where threat modeling comes in, revealing risks and enabling you to tackle them directly. This guide will take you through the essential steps of threat modeling. You’ll learn to identify, assess, and mitigate potential security threats. By the end of this post, you’ll have practical strategies to enhance your app’s security, covering everything from defining the scope and identifying threats, to developing effective mitigation strategies.
Step 1: Define the Scope
Asset Identification
Identify and catalog all critical assets within your SaaS application. Start with sensitive data, including customer information, financial records, and personally identifiable information (PII). Data classification tools based on sensitivity and regulatory requirements will be used to categorize this data.
Next, focus on user credentials, ensuring you implement strong authentication mechanisms like multi-factor authentication (MFA) and secure storage solutions such as hashing and salting passwords. Finally, assess your proprietary code by conducting code reviews and implementing version control systems to track changes and protect intellectual property.
Boundary Determination
Define the scope of your system by mapping out all its components. Use network diagrams to illustrate system boundaries, highlighting where your application interacts with third-party services, APIs, and external dependencies.
Identify each entry and exit point and document all data flows between components. Implement security controls such as API gateways, firewalls, and intrusion detection systems at these boundaries. Additionally, conduct regular reviews of third-party services to ensure they meet your security standards and comply with relevant regulations.
Business Objectives and Risk Tolerance
Align your security strategy with your business objectives and determine acceptable levels of risk. Conduct a business impact analysis (BIA) to understand how security incidents could affect your operations. Use this analysis to set risk tolerance levels, prioritizing risks that could significantly impact your business.
Develop a risk management framework that includes risk assessment methodologies, such as qualitative and quantitative risk analysis. Implement security controls that balance protection with performance, ensuring that your security measures support rather than hinder your business goals. Regularly review and adjust your risk tolerance levels to reflect changes in your business environment and threat landscape.
Step 2: Identify Threats
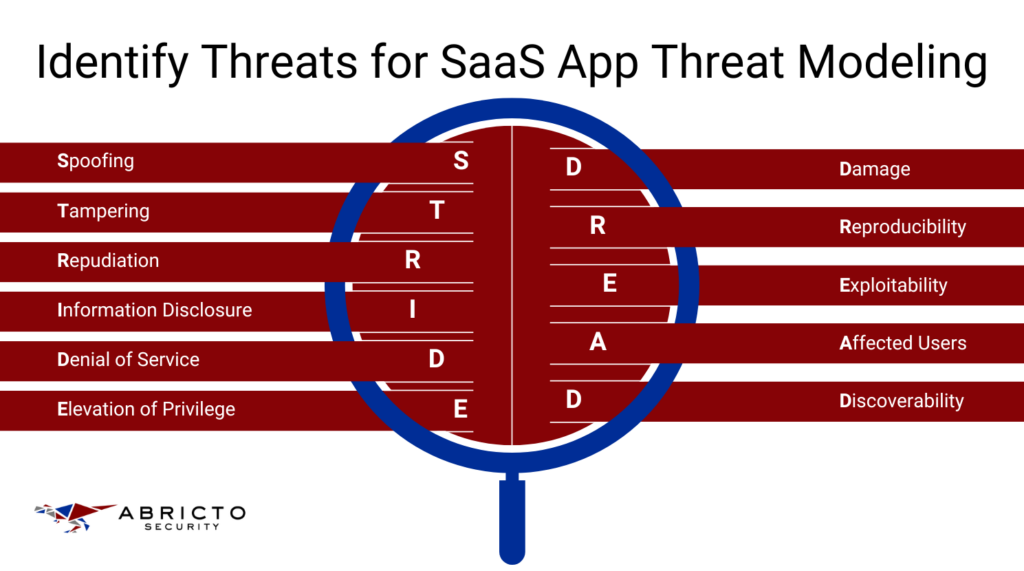
Framework Utilization
Employ established threat modeling frameworks like STRIDE and DREAD to identify potential threats to your SaaS application. STRIDE helps categorize threats into six distinct types: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
Each category highlights specific vulnerabilities and attack vectors to consider. On the other hand, DREAD provides a method to evaluate threats based on Damage, Reproducibility, Exploitability, Affected Users, and Discoverability. By systematically applying these frameworks, you can ensure a thorough examination of potential security risks, enabling you to prioritize and address them effectively.
Stakeholder Brainstorming
Engage in threat brainstorming sessions with your developers, DevOps, and security teams. These collaborative discussions bring diverse perspectives and expertise to the table, helping to uncover threats that might otherwise be missed.
Schedule regular brainstorming meetings and encourage open dialogue where team members can share insights on potential vulnerabilities and attack vectors. Document all identified threats and categorize them for further analysis. This collaborative approach enhances threat identification and fosters a culture of security awareness within your organization.
Threat Intelligence
Leverage threat intelligence feeds and databases to stay informed about the latest vulnerabilities and attack techniques. Resources like MITRE ATT&CK, OWASP Top Ten, and CVE databases provide information on current threats and common vulnerabilities.
Integrate these feeds into your security operations for real-time updates on emerging threats. Use this intelligence to update your threat models and refine your security measures continuously. By staying informed, you can proactively defend against new attack vectors and ensure your security posture remains resilient against evolving threats.
Step 3: Create a Threat Model Diagram
Data Flow Diagrams (DFDs)
Let’s start by creating Data Flow Diagrams (DFDs) to map out how data moves between different components of your SaaS application. Imagine drawing a map of your data’s journey from when a user inputs information to when it’s processed and stored.
Highlight every entry and exit point along the way. This visual representation helps you see where your data could be vulnerable and ensures you have the right security measures at each step.
Trust Boundaries
Next, let’s talk about trust boundaries. These are the points in your system where data moves from a trusted area to an untrusted one. For example, data from a user’s browser to your server crosses a trust boundary.
Marking these boundaries in your DFDs helps you identify where you need extra security, like encryption or authentication. Clearly defining these zones makes it easier to spot and protect potential weak points in your system.
Tools
To make this process easier, let’s use some handy tools designed for creating threat models. Tools like Microsoft Threat Modeling Tool, OWASP Threat Dragon, and ThreatModeler are great for visualizing and documenting your threat model.
These tools allow you to draw your DFDs, mark trust boundaries, and keep track of potential threats in a structured way. Using these tools makes the process smoother and ensures you have a detailed and accessible record for ongoing security assessments and updates.
Step 4: Analyze Threats
Risk Assessment
Begin risk assessment by evaluating the likelihood and impact of the identified threats. Use qualitative and quantitative methods to get a full picture.
For qualitative analysis, you can rely on expert judgment and historical data to gauge the likelihood of a threat’s occurrence and impact. Use metrics and statistical models to provide more concrete data for quantitative analysis. This dual approach ensures you thoroughly understand each threat’s potential effects on your system.
Prioritization
Once you’ve assessed the risks, it’s time to prioritize them. Create a risk matrix to rank these threats based on their likelihood and impact. This visual tool helps you see which threats pose the most significant risk so you can focus on addressing high-priority threats first.
Prioritizing helps allocate resources efficiently, ensuring that the most severe and likely threats are managed before the less critical ones.
Threat Scenarios
Now, let’s develop realistic threat scenarios and attack trees. These tools help you understand how potential attacks might unfold. A threat scenario is a detailed narrative of a potential attack, describing each step an attacker might take.
An attack tree breaks down these steps into a branching diagram, showing various paths an attacker could take to exploit a vulnerability. By visualizing these scenarios, you can better anticipate attack methods and strengthen your defenses accordingly.
Step 5: Develop Mitigation Strategies
Start by mapping each identified threat to specific security controls and countermeasures. This means looking closely at each threat and determining which security measures can effectively mitigate it.
For instance, if you’ve identified a threat related to data tampering, you might implement integrity checks and cryptographic controls. Creating this map helps ensure that every identified threat has a corresponding security measure to address it, making your system more resilient.
Next, we’ll implement a defense-in-depth strategy by adding multiple layers of security controls. Think of it as building layers of protection around your assets. Start with encryption to protect data both in transit and at rest.
Add access controls to ensure only authorized users can access sensitive data and systems. Implement intrusion detection systems to monitor and alert you to potential security breaches. These layered defenses work together to provide a more comprehensive security posture.
Step 6: Validate and Test
Security Testing
First, ensure your security measures are effective by conducting thorough security testing. This includes penetration testing, where ethical hackers try to exploit vulnerabilities just like a real attacker would.
Perform network and application vulnerability scanning to identify weaknesses in your system that could be exploited. Additionally, conduct regular code reviews to catch and fix security issues in your codebase. These tests help ensure your defenses are solid and capable of withstanding attacks.
Automated Tools
Next, integrate automated security testing tools into your CI/CD pipelines. Use static application security testing (SAST) tools to analyze your code for vulnerabilities before it’s compiled.
Dynamic application security testing (DAST) tools can simulate attacks on your running applications to identify security gaps. These automated tools provide continuous feedback on your security posture, helping you catch issues early and often, keeping your applications secure throughout the development lifecycle.
Continuous Monitoring
Implement continuous monitoring and logging to monitor potential security incidents. Set up real-time monitoring systems to track activities across your network and applications.
Logging, which records all events, can be invaluable for detecting unusual behavior and conducting forensic analysis after an incident. This proactive approach allows you to detect and respond to security threats quickly, minimizing potential damage and maintaining the integrity of your systems.
Step 7: Document and Maintain

Documentation
Start by keeping detailed documentation of your threat model. This includes all identified threats, the mitigation strategies you’ve implemented, and the results from your security testing.
Having this information well-documented ensures that everyone on your team is on the same page and that you have a clear record to refer back to. It also makes reviewing and updating your security measures easier as needed.
Regular Updates
Next, make it a habit to update your threat model regularly. As your application evolves—whether through changes in architecture, new code, or shifts in the threat landscape—your threat model should reflect these changes.
Schedule periodic reviews and updates to ensure your security measures remain relevant and effective. Keeping your threat model current helps you avoid potential risks.
Ongoing Assessment
Finally, a process for ongoing threat assessment and risk management must be established. This means continuously evaluating your security posture and adjusting your defenses as new threats emerge.
Conduct risk assessments regularly to identify new vulnerabilities and ensure your mitigation strategies are up to date. By committing to ongoing assessment, you can proactively manage risks and maintain a strong security posture over time.
Leveraging AppSec as a Service
Consider exploring AppSec as a Service offering to boost your security without needing extensive in-house resources. This service provides specialized security solutions tailored to your needs, helping you implement and maintain strong security practices. By leveraging this external service, you can enhance your security posture efficiently and focus more on your core business operations.
Managed Security
Take advantage of managed security services for continuous threat monitoring, vulnerability assessments, and incident response. These services constantly monitor your system, identifying and mitigating threats in real time. Managed security providers bring expertise and tools that might be difficult to maintain internally, ensuring your SaaS application stays secure around the clock.
Scalability
One of the great benefits of using AppSec as a Service is its scalability. As your SaaS application grows, these services can easily scale with you. This flexibility allows you to manage security cost-effectively, ensuring that your security measures can expand to meet increased demands without significantly increasing costs or complexity.
Expertise
Leveraging AppSec as a Service gives you access to security experts and the latest threat intelligence. These professionals are constantly up-to-date with emerging threats and vulnerabilities, helping you avoid potential risks. By tapping into their expertise, you can ensure that your security practices are cutting-edge and your SaaS application is well-protected against evolving threats.
Conclusion
We’ve covered the key steps to effectively threat model your SaaS application: defining the scope, identifying threats, creating threat model diagrams, analyzing threats, developing mitigation strategies, and keeping your threat model current. If you’re ready to boost your SaaS app’s security book a call with us today to learn more.
