Our team researches and documents bleeding-edge security concepts and hacking techniques.
This blog explores these topics and more to keep you informed.
HTB: Blocky Walkthrough
Blocky is a Linux machine with an easy-to-medium difficulty rating. It contains several intentional rabbit holes, including WordPress components, plugin directories, and PhpMyAdmin, which can initially mislead the enumeration process. Nmap Scan ┌──(kali㉿kali)-[~] └─$ nmap ...
Understanding #s in C Programming Part 1: Macros and Conditionals
Within C programming, there are many commands that start with the # symbol that are used as placeholders for the C preprocessor. These hash-directives can be used to define tokens for substitution, pull in header ...
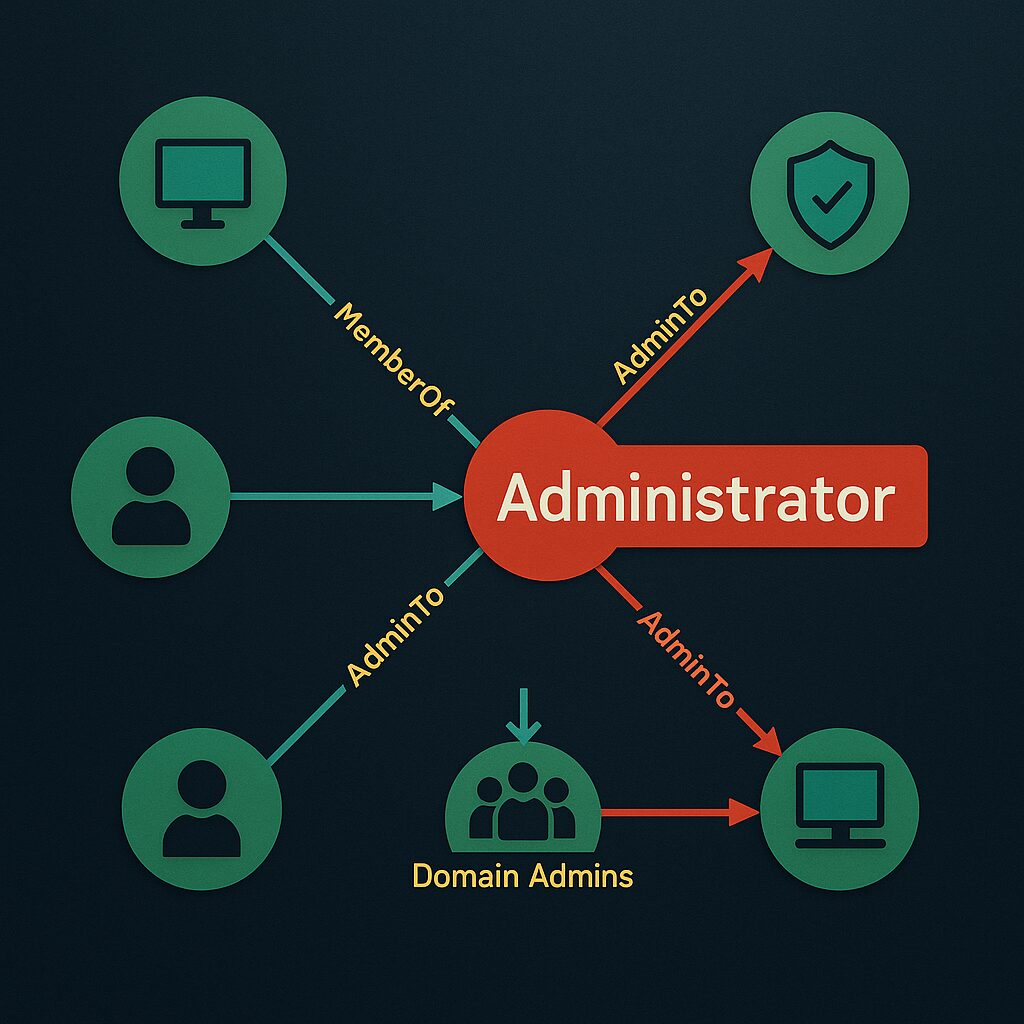
HTB: Administrator Walkthrough
Administrator is a Windows-based machine rated as medium difficulty on Hack The Box. It’s designed to mimic a real-world Active Directory setup, giving the opportunity to dig into SMB enumeration, map out attack paths with ...
Attacks You Should Know About: Clickjacking
Welcome back to another installment of "Attacks You Should Know About"! If you’ve been following along, you already know that web applications are full of potential vulnerabilities. Today, we’re diving into one of the more ...
HTB: MonitorsTwo Walkthrough
MonitorsTwo is an Easy-difficulty Linux machine on Hack The Box that offers a comprehensive exploration of various vulnerabilities and misconfigurations. It starts off with a web application that is vulnerable to an unauthenticated remote ...
The Dangers of HTTP Headers
When talking about the threat landscape for web applications, you might first think of SQL injections, cross-site scripting, and other well-known attacks. But, there are another vectors that often fly under the radar: HTTP ...
ESC15: The Evolution of ADCS Attacks
ESC15? Never met the guy: ESC15 is unlike any previous ESC vulnerability as it is not a misconfiguration within a template. ESC15 is a vulnerability within Microsoft’s implementation of the Extended Key Usage (EKU) dubbed ...
Proactive Vulnerability Management: Securing Your FinTech SaaS Platform
Introduction FinTech SaaS platforms are transforming the financial industry with innovative solutions and services. However, securing sensitive financial data is more important than ever as security threats continue to mature and evolve. Proactive vulnerability management ...
Implementing ASaaS: A Seamless Transition Guide for SaaS Companies
Introduction Are you looking to improve your company's SaaS security without all the hassle? Switching to Application Security as a Service (ASaaS) can be a game-changer. It offers continuous monitoring, expert support, and automated compliance, ...