Our team researches and documents bleeding-edge security concepts and hacking techniques.
This blog explores these topics and more to keep you informed.
SaaS Security Fundamentals: Building a Strong Security Posture for Your SaaS Application
Introduction Have you ever wondered how the top Software as a Service (SaaS) platforms keep their data safe? This article will explore the core concepts of securing SaaS applications. It's packed with essential tips and ...
Learning About SSL/TLS Certificates – Part 1
The Beginning: If you were around for the early days of the internet, you can remember the awe of navigating through dozens of websites and chatrooms. Getting recommended new sites from friends you just made ...
Common Mistakes SaaS Businesses Make With Application Security
Introduction Is your SaaS platform's security armor full of chinks you've yet to discover? As we explore the essential role of application security in the SaaS sector, this article will cover why regular security audits ...
Privilege Escalation on macOS: Leveraging Common Techniques
Introduction I am a firm believer that given enough time and resources, vulnerabilities can be found in any platform. Sometimes they are hard, sometimes they are easy, but they are there. ...
Network Poisoning Scanner with Trafficscan.py
Anyone that has ever had to deal with an internal network penetration test knows the big 3 of network poisoning attacks. Those are Link Local Multicast Name Resolution (LLMNR), Network Basic Input/Output System (NetBios), ...
Escapes Evading Environmental Entities Entirely
The latest hacking scheme of the XZ Utils vulnerability showcases the importance of code review. We can view different files as a raw file in something like Github. How often have you received or reviewed ...
Windows Subsystems for Linux – What is it and How to Proxy Web Traffic to BurpSuite
As you walk the path to becoming an ethical hacker, you begin realize that one of the greatest skills in this profession is your ability to learn and adapt to new tools and technologies. Recently, ...
XSS to NTLM Leak using MSQuery
Recently, a paper regarding a new CVE was published by Varonis about multiple exploits to coerce Net-NTLM authentication. One of these methods abuses how explorer.exe handles search queries for files. Web browsers can open applications ...
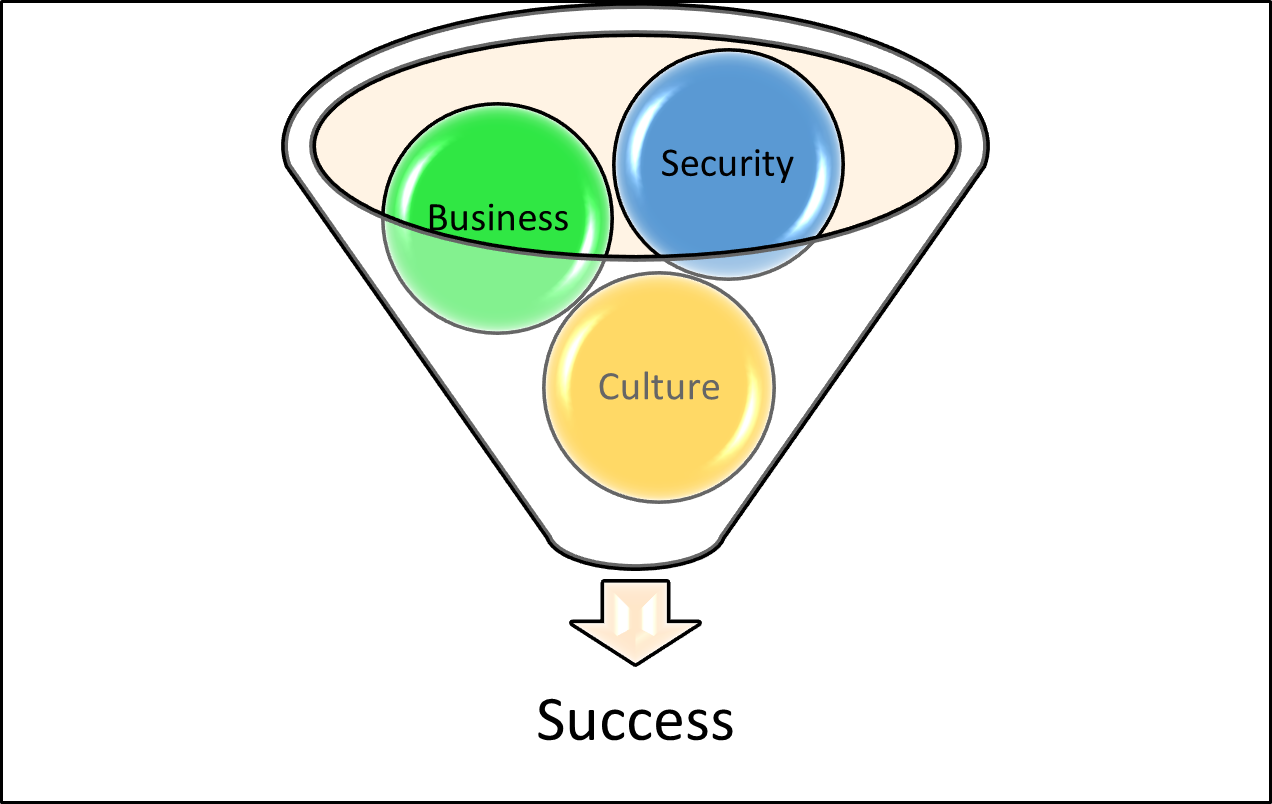
The Triumvirate of Success: Security, Business, and Culture
As fast pace as the world is, cyber threats lurk at every corner. As business and technology leaders, we have a certain level of responsibility to safeguard our organization's assets while simultaneously fostering a growth-oriented ...