Our team researches and documents bleeding-edge security concepts and hacking techniques.
This blog explores these topics and more to keep you informed.
PHP Type Juggling
Type juggling is an expected functionality of PHP when leveraging loose comparisons. However, it can be used to subvert intended operations. In this blog, we will discuss why type juggling occurs, what are the potential ...
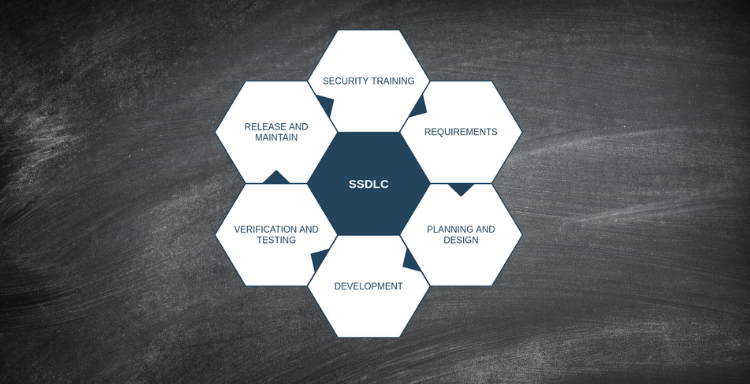
Defining the Secure Software Development Lifecycle (SSDLC)
Here at Abricto Security, we believe that application penetration tests only reveal the tip of the iceberg. Specifically, if we conduct an application penetration test and we find that it’s riddled with vulnerabilities, the remediation ...
Our Response to COVID-19
Abricto Security understands that all industries feel the impact of COVID-19 and we’re here to help. Our team is shifting our operating procedures to accommodate fully remote consultations and assessments. Here is how we plan ...
SQLmap Cheatsheet and Examples
Target the http://target.server.com URL using the "-u" flag: sqlmap -u 'http://target.server.com' Specify POST requests by specifying the "--data" flag: sqlmap -u 'http://target.server.com' --data='param1=blah¶m2=blah' Target a vulnerable parameter in an authenticated session by specifying cookies using the "--cookie" ...
Extracting Private Keys From Public Keys Generated With Weak Random Number Generators
Public key encryption is heavily utilized in modern implementations of SSH. By leveraging public key cryptography, administrators can generate both a public key and a private key to encrypt and decrypt data in transit. Using ...
Password List Generation Using CUPP
In many of our network and web application penetration tests, we come across login portals that aren't protected by anti-automation controls. Essentially, this allows us to launch unrestricted dictionary attacks on previously identified usernames. When ...