Our team researches and documents bleeding-edge security concepts and hacking techniques.
This blog explores these topics and more to keep you informed.
Are Your Cybersecurity Investments In Tools and Services Paying Off?
Finding, implementing, and supporting cybersecurity tools and services within an organization can be a daunting task for a company of any size. There is no shortage of cybersecurity tools and services available to address just ...
Why Critical Vulnerabilities Like Log4Shell Will Continue to Surface
What is Log4Shell? Log4Shell is a critical vulnerability that affects the Log4J Java logging library (versions 2.14.0 and earlier) bundled into the Apache logging services. The vulnerability allows remote code execution (RCE) by a malicious ...
Hacking 101: Getting Your Bearings
Network security is a unique field of IT, and unlike many other IT fields, it seems almost hostile to anyone new and looking to learn about pentesting. I’ve heard several statements that boil down to ...
User Enumeration in a Production Environment – Credential Stuffing 101
Ah yes, credential stuffing! Almost as common as thanksgiving stuffing, yet as distasteful as black Friday shopping. Credential stuffing is especially effective when it’s coupled with user enumeration. The likelihood of user enumeration attacks occurring ...
Dangling DNS: Low Hanging Fruit with Severe Consequences
In this blog we discuss dangling DNS and how if left unresolved, an attacker can mar the reputation of a victim company. First let's start by defining Domain Name System (DNS). A Domain Name System ...
Exploiting Bring Your Own Device (BYOD)
Bringing your own device (BYOD) is a common practice within many organizations and due to COVID-19, the adoption of BYOD has expanded. The belief that software or applications can protect data from bad actors or ...
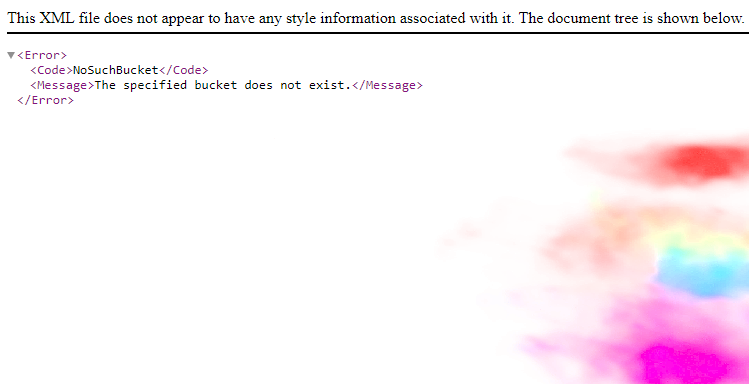
Command and Control Through AWS S3 Buckets
Many organizations leverage AWS as their cloud computing platform. Allowing access to and from their AWS resources is critical for workloads to operate uninterrupted. This means that an AWS VPC is often seen as a ...
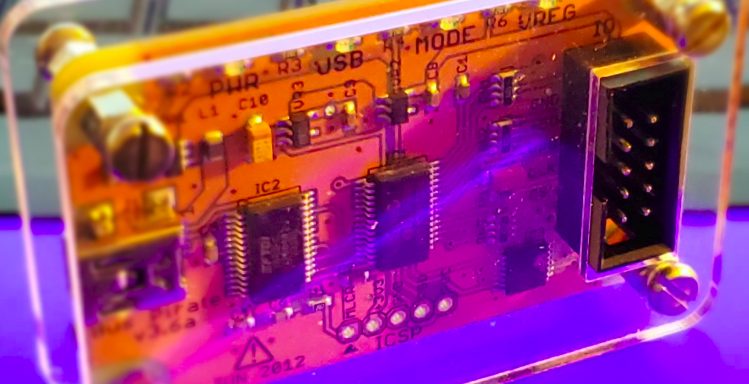
Introduction to Hardware Hacking: Part 2
In the last blog, we discussed the components that are used in hardware hacking, the discovery phase and how to pull information off a device leveraging a UART port and the Das U-Boot boot loader. ...
Introduction to Hardware Hacking: Part 1
There are many devices out there that store information in different ways and unfortunately, not all of them take security into account. With the advent of the Internet of Things (IoT), device manufacturers are publishing ...