Our team researches and documents bleeding-edge security concepts and hacking techniques.
This blog explores these topics and more to keep you informed.
The Dangers of HTTP Headers
When talking about the threat landscape for web applications, you might first think of SQL injections, cross-site scripting, and other well-known attacks. But, there are another vectors that often fly under the radar: HTTP ...
ESC15: The Evolution of ADCS Attacks
ESC15? Never met the guy: ESC15 is unlike any previous ESC vulnerability as it is not a misconfiguration within a template. ESC15 is a vulnerability within Microsoft’s implementation of the Extended Key Usage (EKU) dubbed ...
Proactive Vulnerability Management: Securing Your FinTech SaaS Platform
Introduction FinTech SaaS platforms are transforming the financial industry with innovative solutions and services. However, securing sensitive financial data is more important than ever as security threats continue to mature and evolve. Proactive vulnerability management ...
Implementing ASaaS: A Seamless Transition Guide for SaaS Companies
Introduction Are you looking to improve your company's SaaS security without all the hassle? Switching to Application Security as a Service (ASaaS) can be a game-changer. It offers continuous monitoring, expert support, and automated compliance, ...
AppSec as a Service for HealthTech SaaS Companies
Introduction In the world of HealthTech, keeping electronic health records (EHR), telemedicine platforms, and patient management systems secure is a challenging issue. That’s where AppSec as a Service comes in. It can greatly improve the ...
How To Threat Model Your SaaS App: A Technical Guide for SaaS Companies
Introduction Do you find protecting your app from the latest security threats challenging? A lot of folks do. This is where threat modeling comes in, revealing risks and enabling you to tackle them directly. This ...
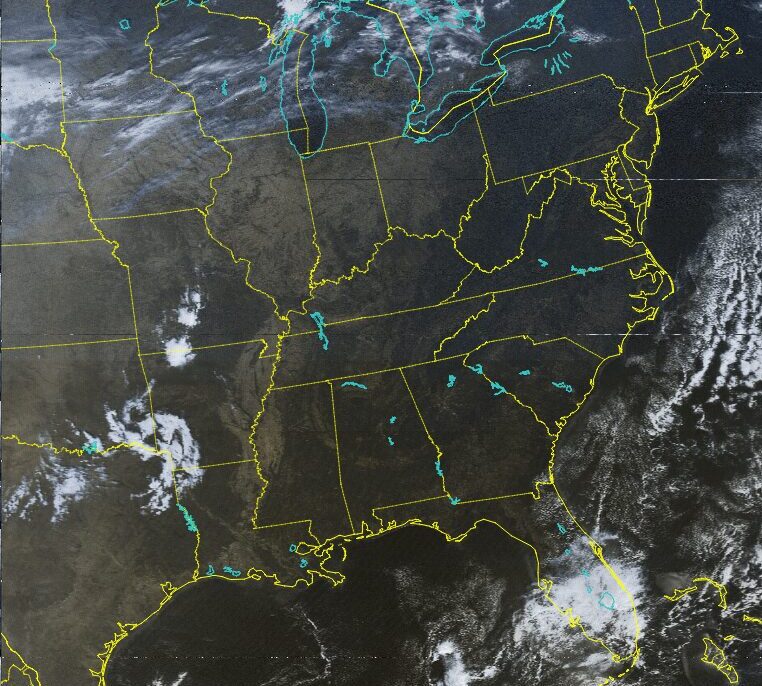
Capturing Live Satellite Images
Imagine watching the world unfold in real-time from space. Witnessing natural events and seeing the world from a new perspective. Well thanks to satellite images you don’t have to imagine too hard. Utilizing some relatively ...
NTLM vs Kerberos Authentication Processes
What are authentication protocols? An authentication protocol is a method used by a server to verify the authenticity of a request, typically ensuring that the user is valid. There are many different authentication protocols; however, ...
Getting Started With CTFs
If you're interested in getting into cybersecurity, try gamifying the experience and familiarize yourself with concepts and tools by joining CTFs! What are CTFs? Capture-the-Flag events are primarily online competitions where teams solve challenges to ...