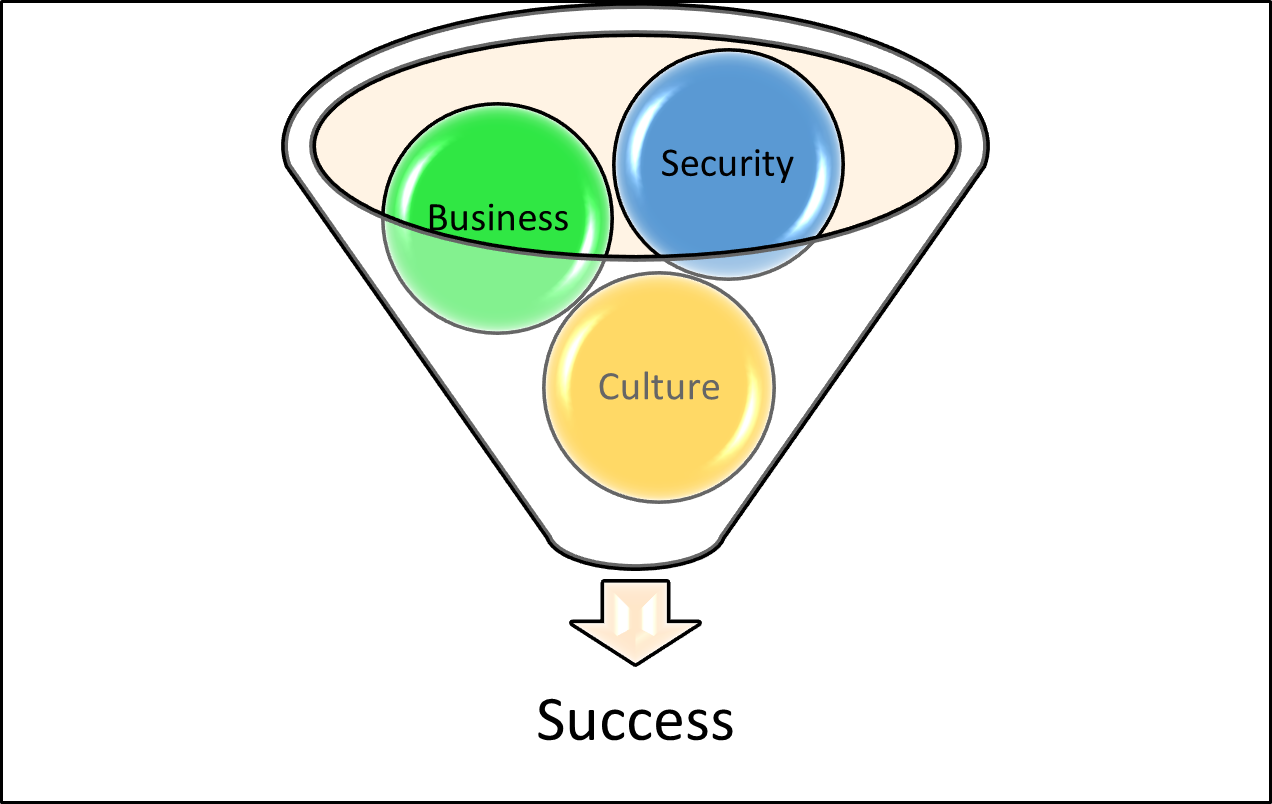
The Triumvirate of Success: Security, Business, and Culture
As fast pace as the world is, cyber threats lurk at every corner. As business and technology leaders, we have a certain level of responsibility to safeguard our organization's assets while simultaneously fostering a growth-oriented ...