Introduction
I am a firm believer that given enough time and resources, vulnerabilities can be found in any platform. Sometimes they are hard, sometimes they are easy, but they are there. In this blog post we delve into how common privilege escalation techniques can be applied to macOS. We will discover how having a core understanding of basic privilege escalation techniques, coupled with a touch of ingenuity, can lead to vulnerabilities in even the biggest names of the tech industry.
Finding the Path: Leveraging Homebrew
The first step of elevating privileges is enumerating common techniques. Once such technique is to find a user writable path where root calls to and runs a function. Would you be surprised to know that such a path exists in macOS? Let’s take a look at /usr/local/bin. A vanilla macOS does not ship with such a path but commonly used add-ons create this path as a user writable path. Once such add-on is Homebrew. Homebrew is a package manager facilitating the addition of tools not included in the default macOS installation. It introduces /usr/local/bin to the system’s PATH environment variable, allowing users to execute custom binaries. By adding Homebrew to your installation, you invoke unrealized risks of privilege escalation. The next step is identifying a target to exploit this newfound path.
Identifying the Target: Exploiting tmdiagnose
We have identified a potential privilege escalation path now let’s find an application to leverage this functionality. Let’s start by searching for binaries that have “/usr/local/bin” as a string. You may say, “well I am no l33t hacker and I hate assembly”. Well no need to fear, grep is here. All we need is grep -rni “usr/local/bin” *, Google-fu, and a little bit on gumption to make this vulnerability a possibility. Once we grep through the macOS binaries, the tmdiagnose binary sticks out as a possible contender. A quick strings run against tmdiagnose can confirm our suspicion. Let’s dive deeper into this function and see how we might exploit it. Below we have a look at the function tmdiagnose with IDA, my favorite disassembler.
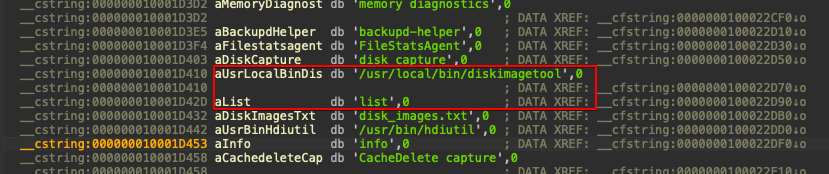
Diving into the mechanics of tmdiagnose reveals its exploitability. This analysis shows that Apple was kind enough to leave comments within the application. We see the application’s call to “/usr/local/bin/diskimagetool” and perform an action named “list” to list disk images. At this point, your security researcher spidey sense should be tingling. We have successfully found a function that calls to /usr/local/bin. If we create a malicious payload named /usr/local/bin/diskimagetool that has a function named list, we can elevate privileges by executing the tmdianose function. See my example below for one such payload.
You are able to grab this payload from my Github over at https://github.com/Auspicious-Rook/macOS-tmdiagnose-priv-esc.
Execution: Tying it all Together
We’ve come so far with just a few simple grep and strings commands but we need to tie it all together. A little Google-Fu shows that the tmdiagnose function can be ran from the CLI but requires sudo. This appears like a dead end, but we decide to try a little harder. Further research shows that the Feedback Assistant tool, which comes on vanilla macOS installs, can initiate the tmdiagnose function without sudo privileges! We have identified the final piece of the puzzle, now let’s see it in action. The attack chains is as follows: Identify /usr/local/bin is user writable, create a malicious function named /user/local/bin/diskimagetool that uses a malicious “list” command, execute the payload through a Time Machine report within the Feedback Assistant application to gain elevated privileges. Enough talk, let’s see it in action!
Mitigation and Remediation: Securing Your macOS Environment
To mitigate the risk of privilege escalation attacks, several preventive measures can be implemented:
- Regularly review and restrict permissions for critical system directories, including /usr/local/bin.
- Implement stringent access controls and user permissions to limit the execution of privileged commands.
- Stay on top of security updates and patches released by Apple, ensuring prompt installation to address known vulnerabilities.
Vendor Negligence: Unresolved Vulnerability in macOS
As security researchers, it’s imperative to spotlight instances where vendors fail to address identified vulnerabilities. In this case, Abricto Security’s Ryan Woodard reported the issue to Apple in September 2022. However, the vendor opted not to address it directly and silently patched the vulnerability with the rollout of Sonama. Regrettably, Apple has conveyed no intentions to implement a fix for macOS versions preceding Sonama. As a result, users operating on Ventura or earlier iterations on Intel and AMD processors remain susceptible to this exploit. Given the severity of the vulnerability, users are advised to take proactive measures, such as removing /usr/local/bin from the system’s PATH variable, to mitigate the risk of exploitation until a comprehensive fix is provided. This highlights the importance of vendor accountability and the necessity for users to remain vigilant in protecting their systems against potential security threats.
Conclusion
The mantra “There is brilliance in the basics” is proven here. The premise and discovery of this vulnerability were basic and utilized strings, grep, and some Google-Fu. Given enough time and resources, vulnerabilities can be found in any platform. So get out there and participate in big vendor vulnerability programs because you never know what you might uncover next!