Our team researches and documents bleeding-edge security concepts and hacking techniques.
This blog explores these topics and more to keep you informed.
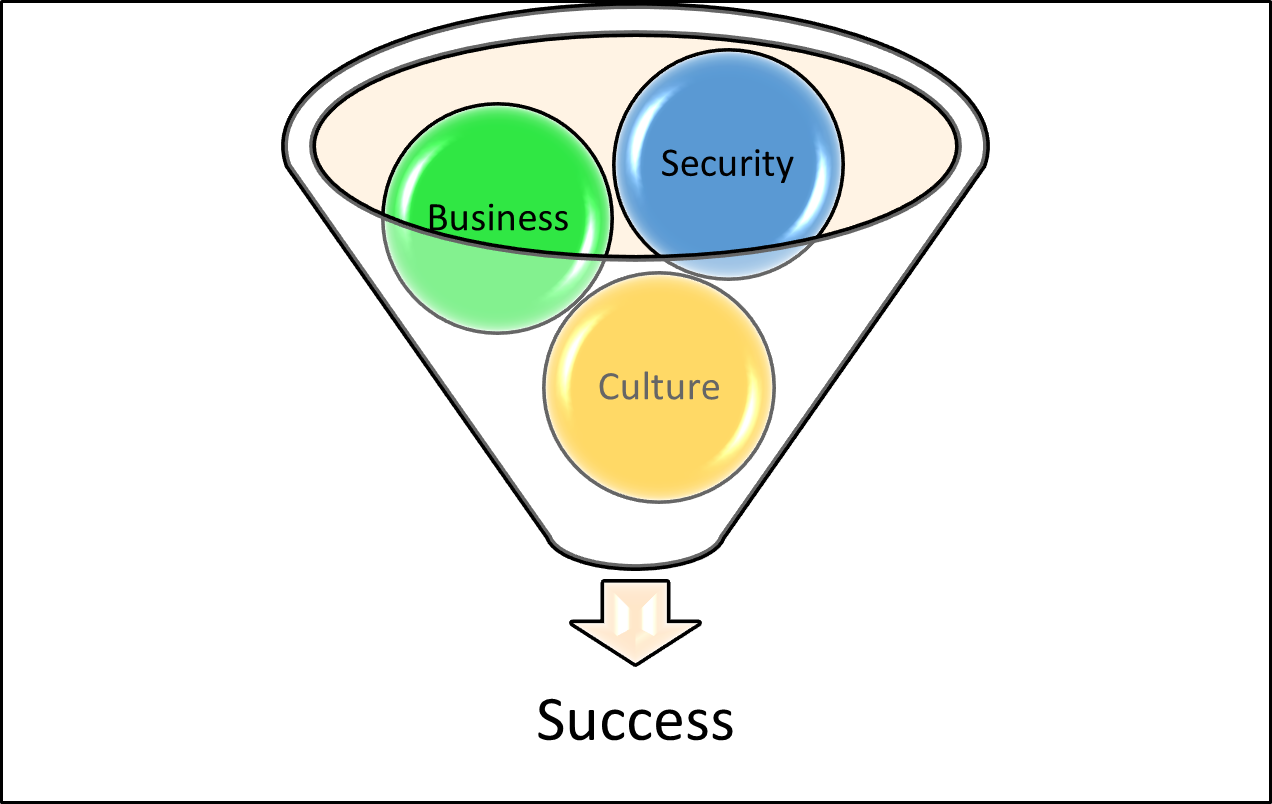
The Triumvirate of Success: Security, Business, and Culture
As fast pace as the world is, cyber threats lurk at every corner. As business and technology leaders, we have a certain level of responsibility to safeguard our organization's assets while simultaneously fostering a growth-oriented ...
Exploiting WordPress Using WPScan
If you’ve ever conducted a web application penetration test, been involved web page development, or hovered within the IT space, you may have heard of a software called WordPress. However, did you know this software ...
CAPTCHA is Dead
History: You want to log into your favorite website. After attempting to enter your password, you make a mistake, and you now need to re-enter your password while also clicking on all the squares with ...
Breaking the Seal: How I Became a Hacker
You Can Do It: Every single person has a journey. No one path can be retraced. This is a story about my personal journey from being in a non-IT related field, to a full-time offensive ...
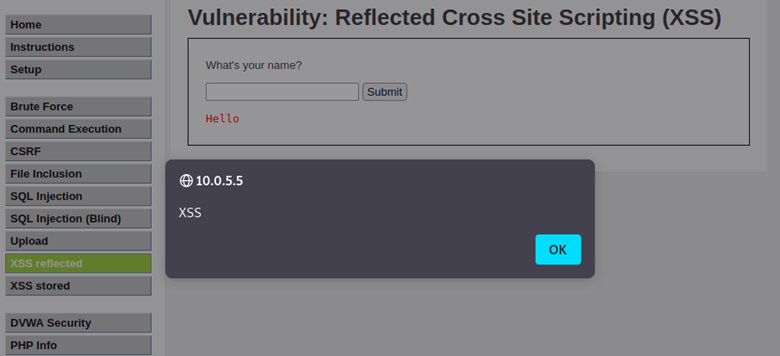
Exploiting Cross-Site Scripting (XSS) Vulnerabilities to Steal Cookies
What are Cookies? While browsing the internet, chances are that you’ve came across pop-ups that ask if you want to allow cookies. Instead of questioning what cookies are, the average user accepts the cookies and ...
Covert Remote LSASS Extraction
What is LSASS and why do we care about it? LSASS stands for Local Security Authority Subsystem Service. It stores passwords and password hashes of: Accounts that are logged into a Windows machine Any other ...
Web Application Injection Cheat sheet
Web applications are the services that websites offer as a way for users to interact with the site. Generally, whenever an end user can interact with an application in some way, their inputs need to ...
Gobuster Directory Enumerator Cheat Sheet
What is Gobuster? Gobuster is a brute-force scanner tool to enumerate directories and files of websites. It will also assist in finding DNS subdomains and virtual host names. Gobuster is written in the Go programming ...
Nmap Network Scanning Cheatsheet
What is Nmap? Nmap is a console based, free port scanning and network mapping tool originally released in 1997 by Gordon Lyon. Nmap allows a user to scan remote or local networks for open ports, ...